篇幅有限
完整内容及源码关注公众号:ReverseCode,发送 冲
抓包
应用层抓包
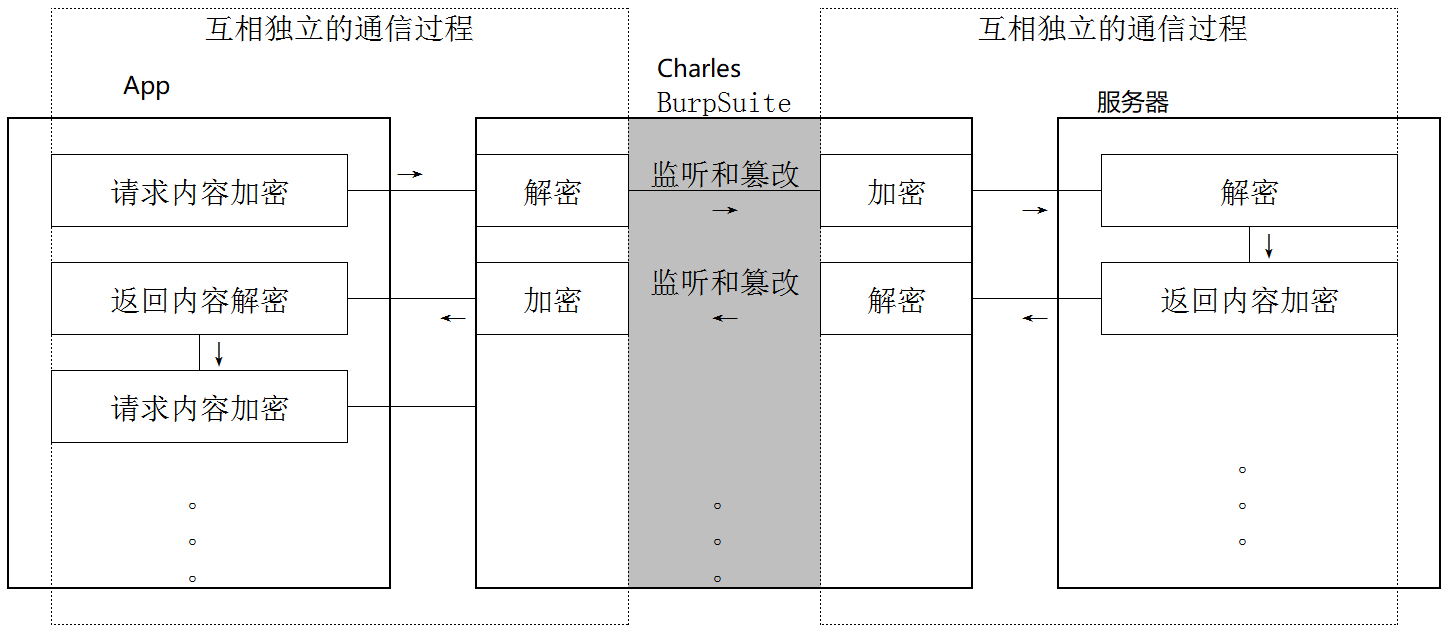
传输层抓包
charles开启Enable socks proxy
wget https://www.charlesproxy.com/assets/release/4.6.1/charles-proxy-4.6.1_amd64.tar.gz?k=17bcbd3dc2
tar zxf charles-proxy-4.6.1_amd64.tar.gz && ./charles 通过注册码注册或生成加权jar包破解
vim ~/.zshrc 并source ~/.zshrc 使得charles在任意路径可启动
1 | export PATH="/root/Android/Sdk/ndk-bundle:/root/Android/Sdk/platform-tools:${JAVA_HOME}/bin:$PATH:/root/Desktop/charles/bin:/root/Desktop/jadx-1.2.0/bin" |
htop 查看破解情况
电脑:192.168.0.106
手机:192.168.0.102
虚拟机:192.168.0.107
虚拟网络编辑器选择获取ip的网卡,保证这三台机器在同一局域网内且互相ping通。
配置charles
socks proxy工作于传输层,更好的观察应用层协议和socks抓包。
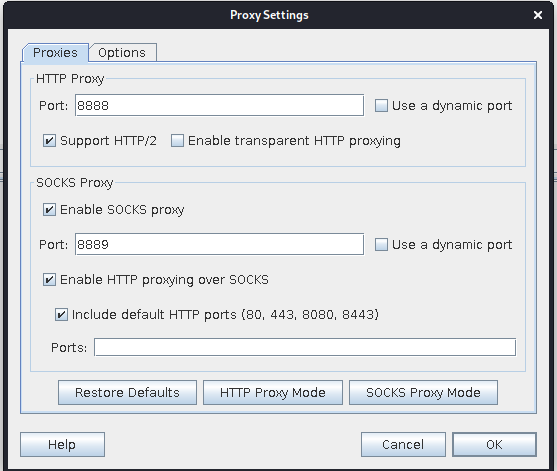
开启ssl
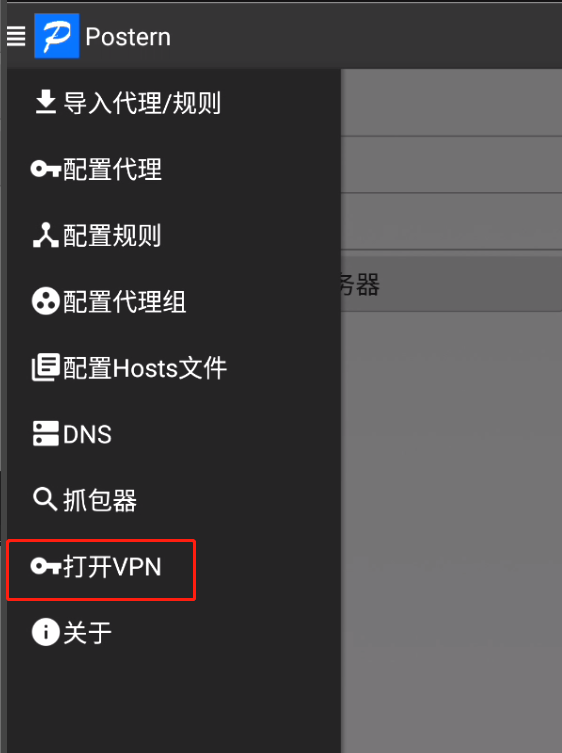
postern
adb install 0714com.tunnelworkshop.postern_2018-10-07.apk
QtScrcpy 设置投屏
配置socks5抓包代理
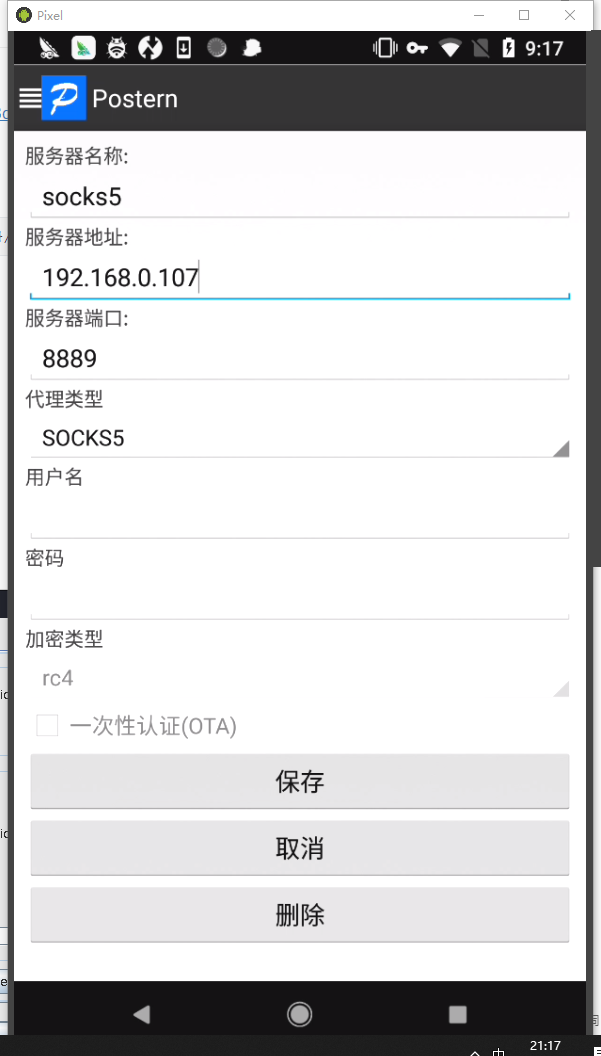
配置socks5抓包配置规则
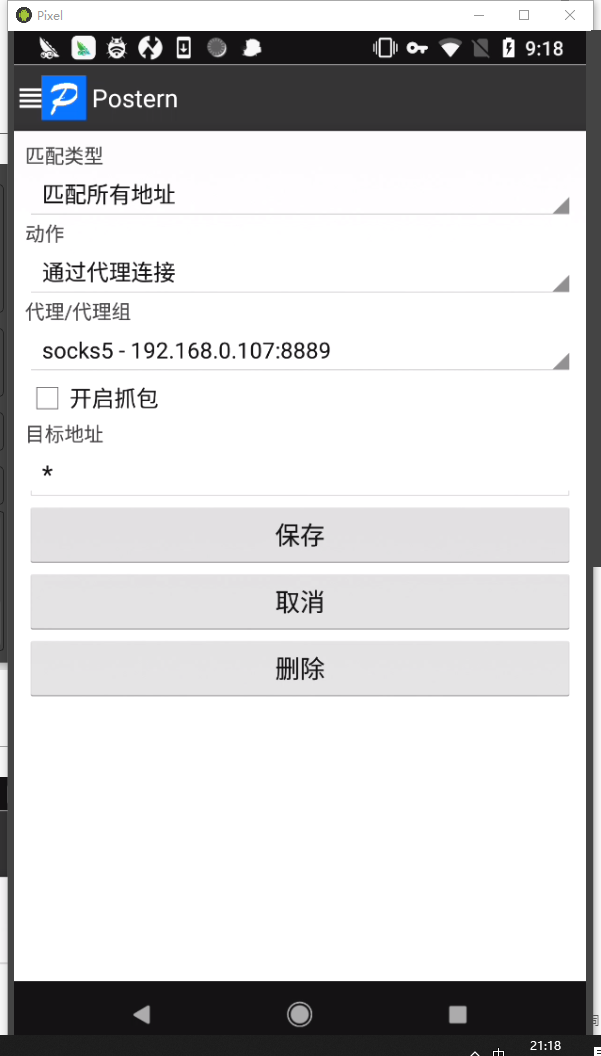
打开socks vpn连接虚拟机抓包,虚拟机收到连接请求后点击Allow
在手机浏览器输入地址 chls.pro/ssl 或者 charlesproxy.com/getssl ,出现证书安装页面,点击安装,如果依旧app抓不到,需要把个人证书放到系统根目录
Android8
2
3
4
5
mount -o remount,rw /
chmod 777 *
cp * /etc/security/cacerts/
mount -o remount,ro /Android 7
2
3
4
5
mount -o rw,remount /system
chmod 777 *
cp * /etc/security/cacerts/
mount -o ro,remount /system
movetv分析
1 | ./fs1428arm64 |
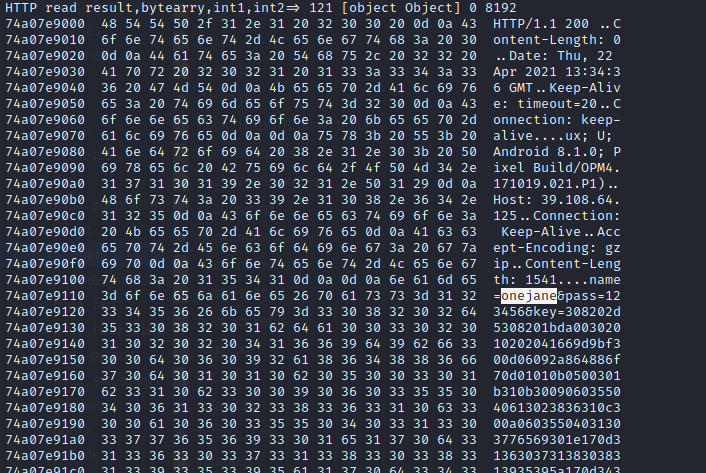
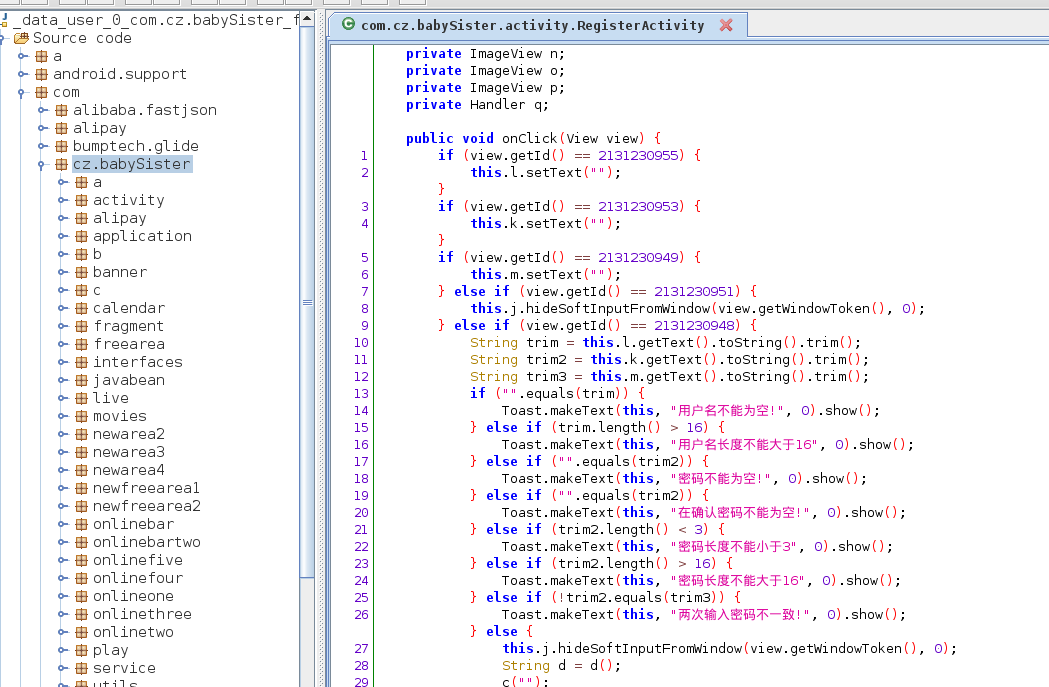
jadx-gui movetv.apk 已经加壳一个Activity都找不到
脱壳
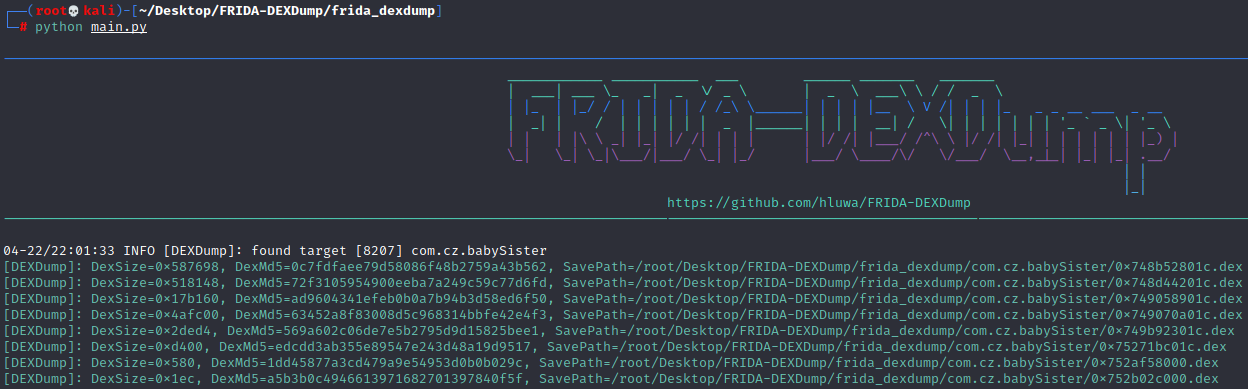
FRIDA-DEXDump
git clone https://github.com/hluwa/FRIDA-DEXDump.git 启动app放在前台
cd ~/Desktop/FRIDA-DEXDump/frida_dexdump && python main.py 开始脱壳
1 | android hooking list activities 查看所有Activity |
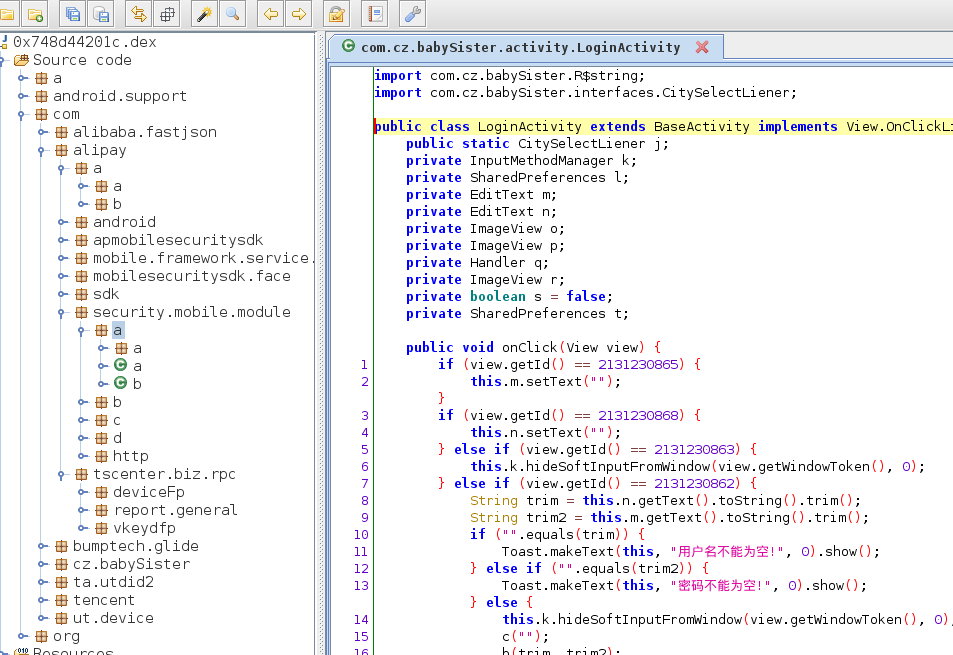
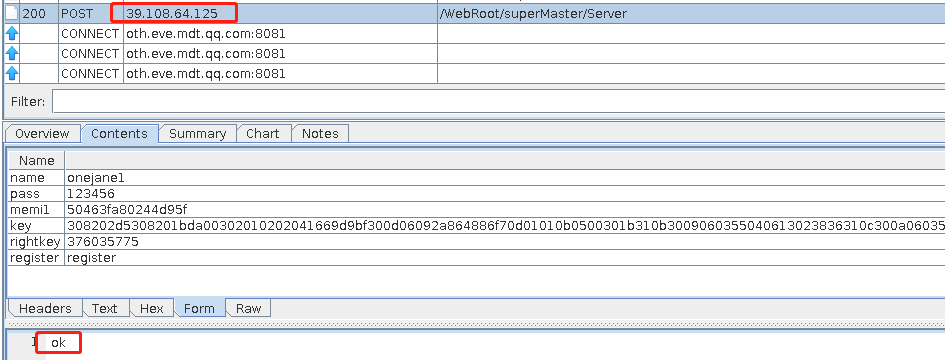
登录
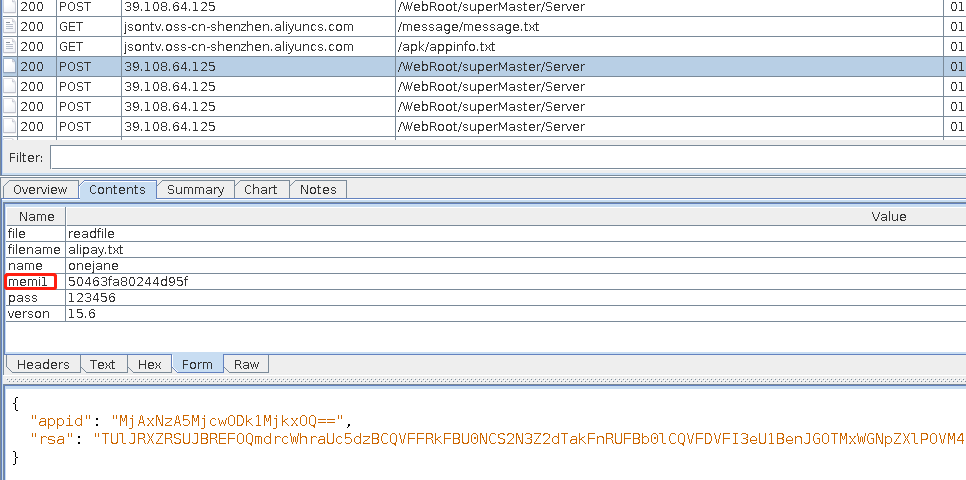
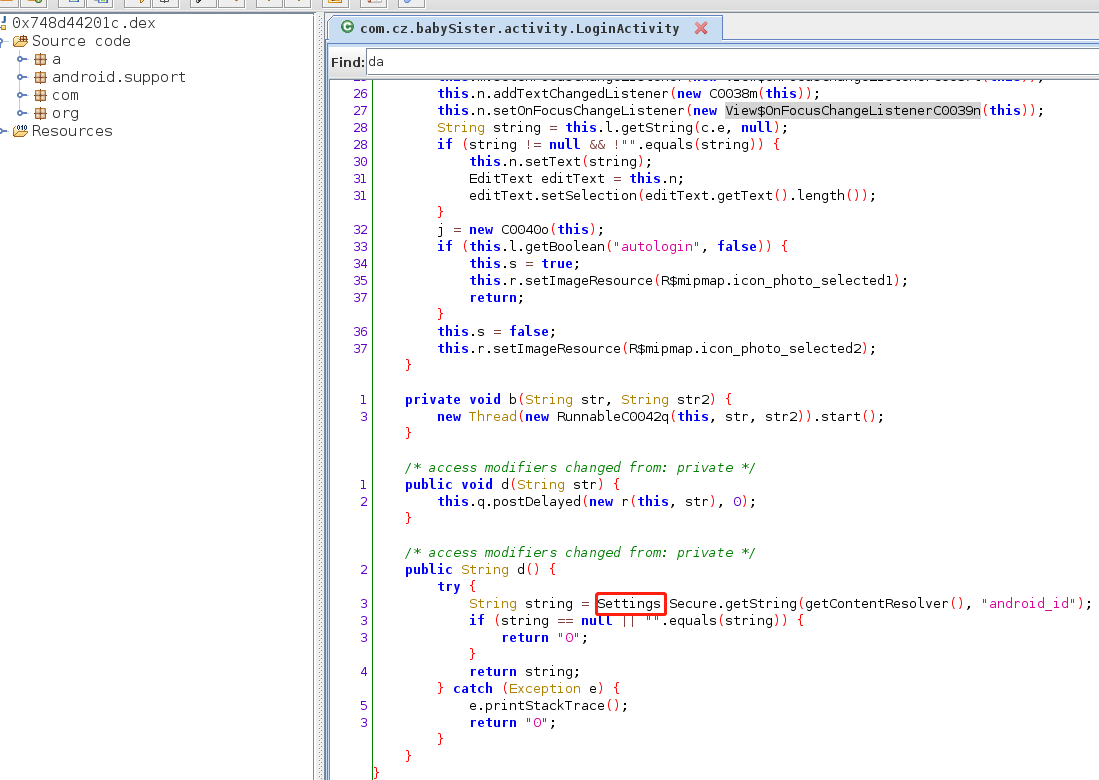
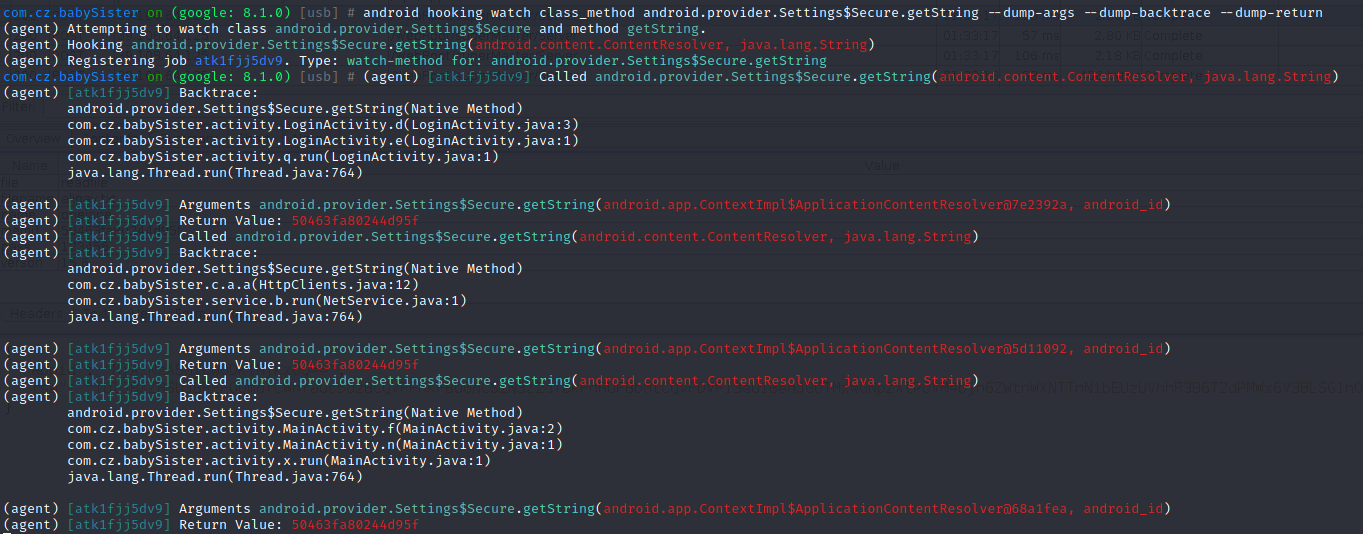
抓登录包获取memi1字段其实来源于android-id
android hooking watch class com.cz.babySister.activity.LoginActivity –dump-args –dump-backtrace –dump-return hook类中所有方法
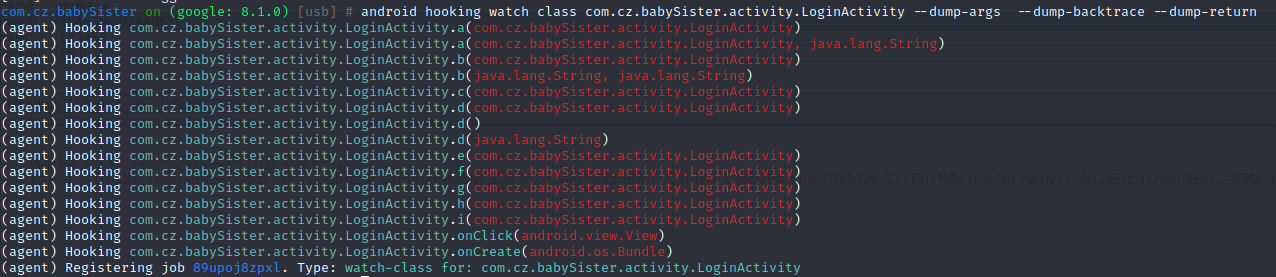
android hooking watch class_method com.cz.babySister.activity.LoginActivity.b –dump-args –dump-backtrace –dump-return hook登录b方法
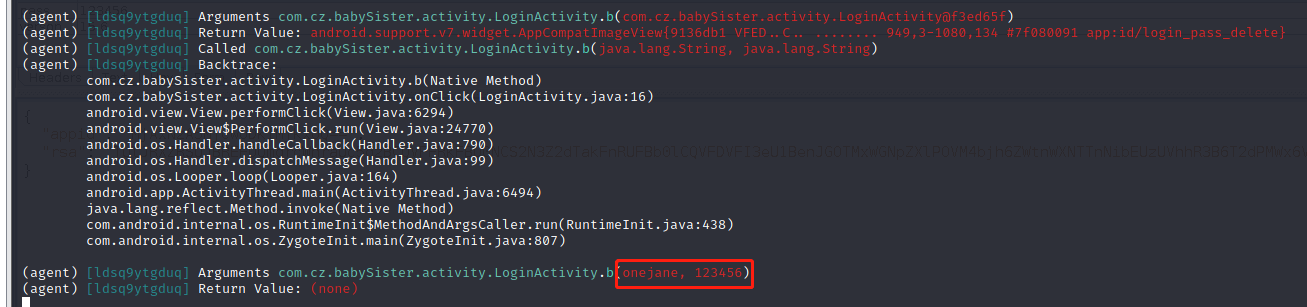
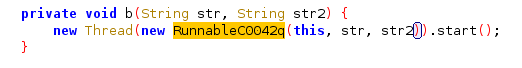
进入b方法中调用的RunnableC0042q类中
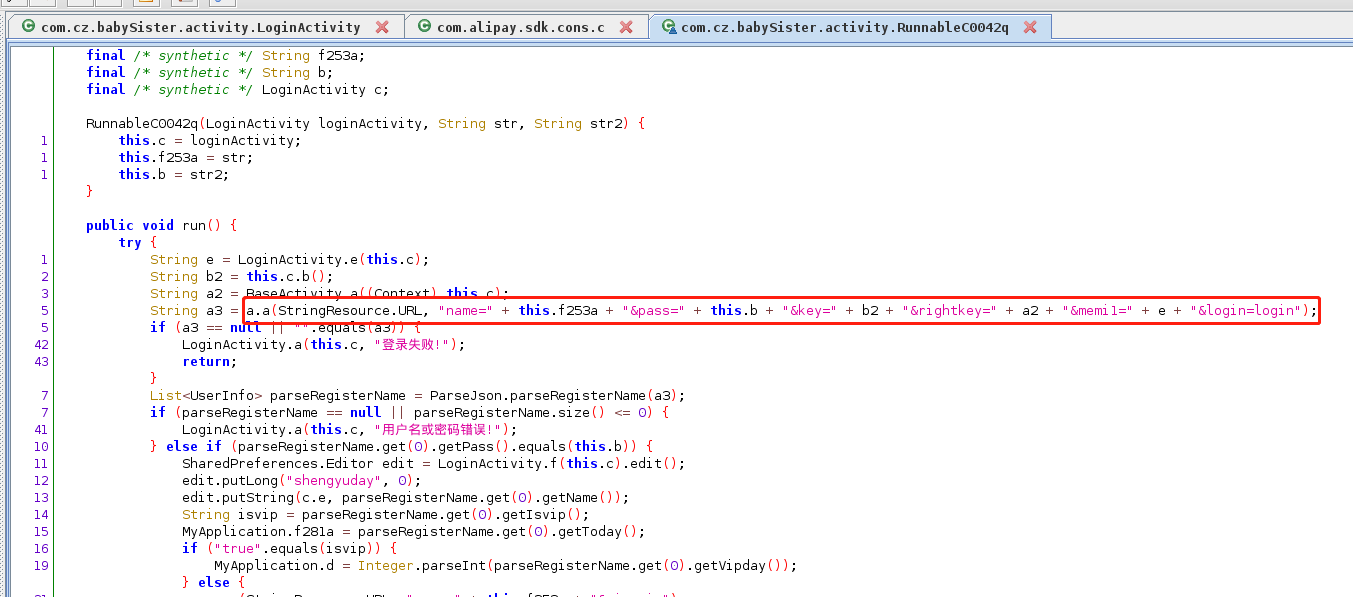
android hooking watch class_method com.cz.babySister.c.a.a –dump-args –dump-backtrace –dump-return hook方法a
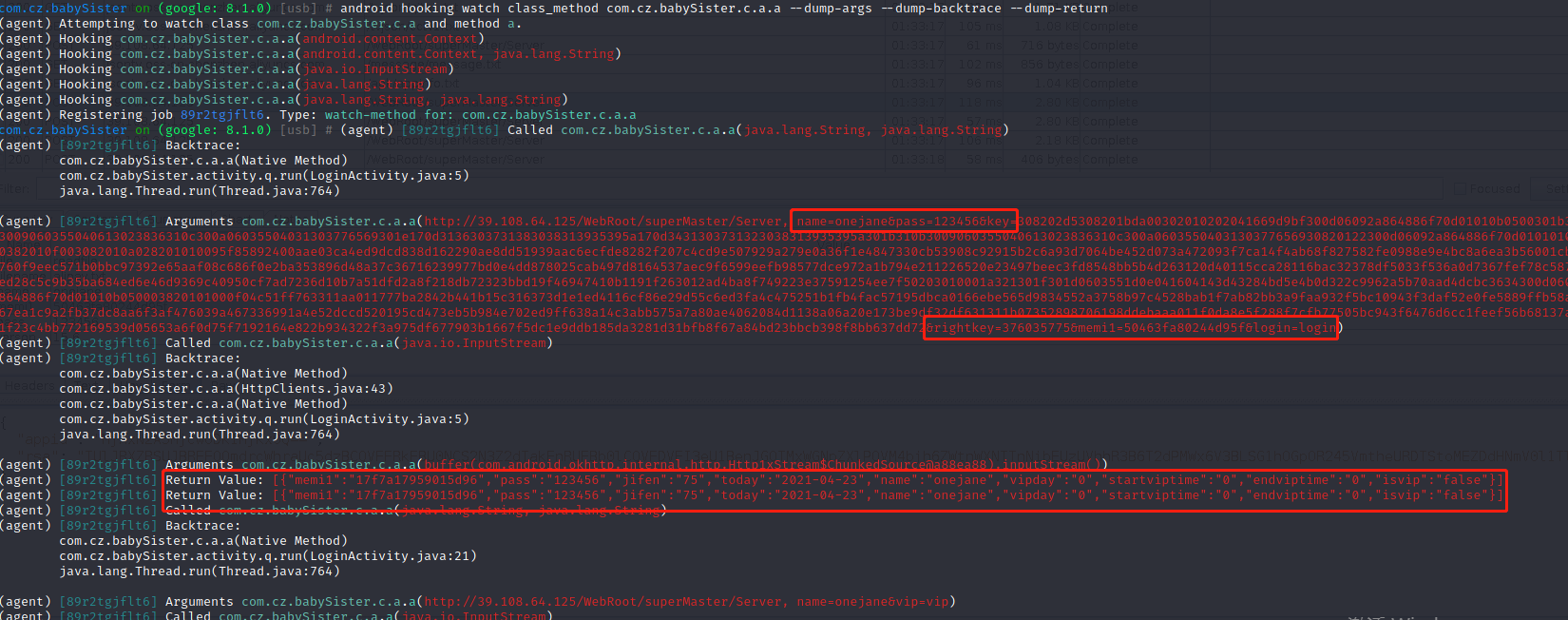
1 | objection -g com.cz.babySister explore |
通过hook获取返回的结果50463fa80244d95f和chales中抓包的memi1完全一致
注册
android hooking watch class_method com.cz.babySister.c.a.a –dump-args –dump-backtrace –dump-return
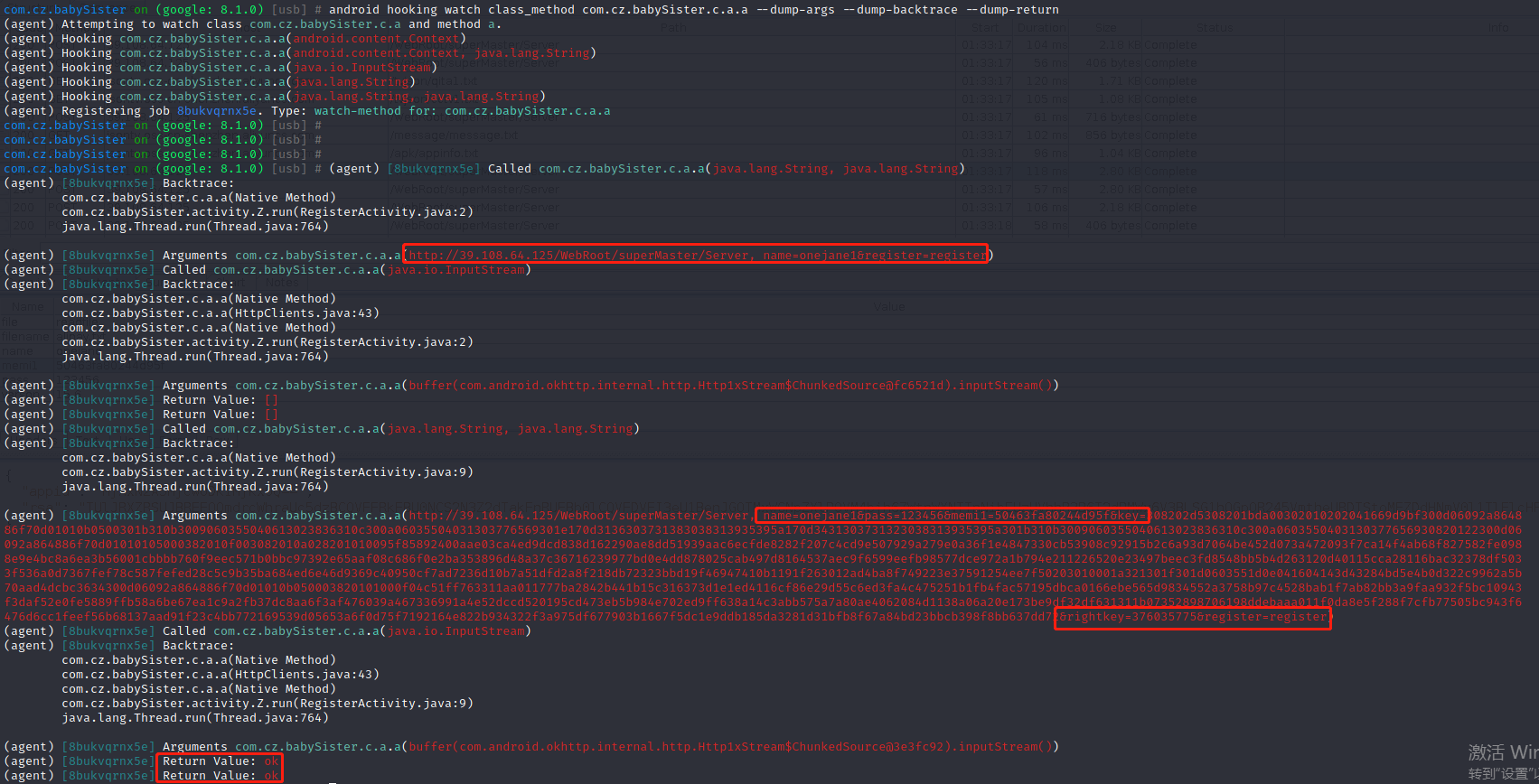
对比抓包结果
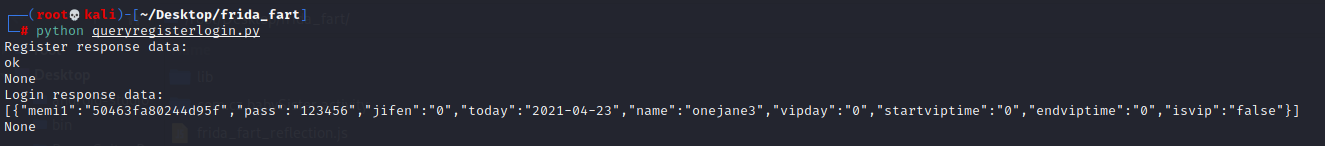
取证实现
1 | import base64 |
Youpk
https://bbs.pediy.com/thread-259854.htm
linux平台下载最新的platform-tools刷机的时候,fastboot会报各种unknow command或接近的错误,把fastboot文件替换成以下随着aosp一起编译出来的即可:
fastboot_aosp7.1.zip
fastboot6.0.zip
fastboot8.1.0r1.zip
下载Youpk_v1.1
- 重启至bootloader:
adb reboot bootloader - 解压 Youpk_sailfish.zip 并双击
flash-all.bat,(尽量在kali上刷机,./flash-all.sh,因为windows会给我们的编程生涯带来80%的苦难)
adb install movetv.apk
adb shell “echo com.cz.babySister >> /data/local/tmp/unpacker.config”
- 启动apk等待脱壳,每隔10秒将自动重新脱壳(已完全dump的dex将被忽略), 当日志打印unpack end时脱壳完成
adb pull /data/data/com.cz.babySister/unpacker/
mv unpacker youpk/
- 调用修复工具 dexfixer.jar, 两个参数, 第一个为dump文件目录(必须为有效路径), 第二个为重组后的DEX目录(不存在将会创建)
java -jar dexfixer.jar youpk/ youpk_out/ jadx-gui _data_app_com.cz.babySister-1_base.apk_54276.dex 查看脱壳后的dex
使用场景
- 整体加固
- 抽取:
- nop占坑型(类似某加密)
- naitve化, 在
中解密(类似早期阿里) - goto解密型(类似新版某加密?najia): https://bbs.pediy.com/thread-259448.htm
问题
- dump中途退出或卡死,重新启动进程,再次等待脱壳即可
- 当前仅支持被壳保护的dex, 不支持App动态加载的dex/jar
fart
脱抽取型壳并回填dex
安装新环境
vim /etc/proxychains4.conf 配置代理
1 | socks5 192.168.0.106 1080 |
主机192.168.0.106 ssr开启运行局域网连接
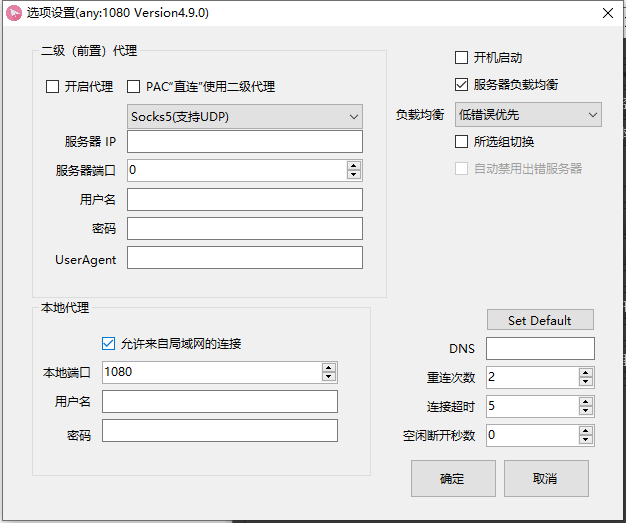
配置新环境
1 | PYTHON_CONFIGURE_OPTS="--disable-ipv6" proxychains pyenv install 3.9.0 创建python3.9.0环境 |
wget frida-server-14.2.16-android-arm64.xz
7z x frida-server-14.2.16-android-arm64.xz
1 | adb push ~/Desktop/frida-server-14.2.16-android-arm64 /data/local/tmp/ |
事实证明,新版本不兼容还是用12.8.0的frida吧
调用fart
基于hook和反射脱壳,对比发现youpk最优秀。
adb reboot bootloader
cd ~/Desktop/sailfish-nzh54d 安卓8.0
./flash-all.sh 刷回去
2
3
4
5
6
7
8
9
10
11
12
13
14
15
adb push magisk-riru-v21.3.zip /sdcard/Download 使用magisk模块安装并重启
adb push magisk-EdXposed-SandHook-v0.4.5.1_beta.4463.-release.zip /sdcard/Download 使用magisk模块安装并重启
adb install EdXposedManager-4.5.7-45700-org.meowcat.edxposed.manager-release.apk 安装xposed
adb push MagiskHidePropsConf-v5.3.4.zip /sdcard/Download
adb install JustTrustMePlus-debug.apk 用于结合xposed突破SSL Pinning抓包限制
adb reboot bootloader
fastboot boot twrp-3.4.0-0-sailfish.img 进入recovery mode
install Magisk-v20.4.zip
adb install MagiskManager-v7.5.1.apk 模块安装MagiskHidePropsConf,riru,EdXposed,
adb shell su通过Magisk获取root权限
settings put global captive_portal_http_url https://www.google.cn/generate_204 去除wifi上的×
settings put global captive_portal_https_url https://www.google.cn/generate_204
settings put global ntp_server 1.hk.pool.ntp.org 修改时区
props Edit MagiskHide props--ro.debuggable 设置全局可调试,getprop ro.debuggable 即可查看1,开启全局可调试
1 | pyenv local 3.8.0 |
1 | adb pull /sdcard/com.cz.babySister.activity |

