篇幅有限 完整内容及源码关注公众号:ReverseCode,发送 冲
刷机 https://developers.google.com/android/images#angler
开机键+音量减 进入recovery
Pixel ES文件浏览器 查看系统文件
玩逆向必备一台真机,那么非谷歌亲儿子莫属,模拟器缺失native/so层,属于精简版系统,故还是真机香呀。
官网 下载pixel 8.1.0镜像 ,建议刷OPM1.171019.011版本安卓8.1.01 2 adb reboot bootloader 或 按住音量向下键和开机键 进入fastboot状态 cd sailfish-opm4.171019.021.p1-factory-0bcf4315/sailfish-opm4.171019.021.p1 && flash-all.sh 开始刷机
设置-关于手机-版本号8下点击-进入开发者模式,进入系统-高级-打开开发者选项-USB调试
1 2 3 4 5 6 adb push Magisk-v20.4.zip /sdcard adb push magisk-riru-v21.3.zip /sdcard/Download 使用magisk模块安装并重启 adb push magisk-EdXposed-SandHook-v0.4.5.1_beta.4463.-release.zip /sdcard/Download 使用magisk模块安装并重启 adb install EdXposedManager-4.5.7-45700-org.meowcat.edxposed.manager-release.apk 安装xposed adb push MagiskHidePropsConf-v5.3.4.zip /sdcard/Download adb install JustTrustMePlus-debug.apk 用于结合xposed突破SSL Pinning抓包限制
twrp 作为第三方刷机工具,刷入Magisk,nethunter等魔改系统。
fastboot flash recovery twrp-3.3.0-0-angler.img
1 2 3 4 5 6 7 8 adb reboot bootloader fastboot boot twrp-3.4.0-0-sailfish.img 进入recovery mode install Magisk-v20.4.zip adb install MagiskManager-v7.5.1.apk settings put global captive_portal_http_url https://www.google.cn/generate_204 去除wifi上的× settings put global captive_portal_https_url https://www.google.cn/generate_204 settings put global ntp_server 1.hk.pool.ntp.org 修改时区 reboot
linux下载最新的platform-tools刷机的时候,fastboot会报各种unknow command或接近的错误,把fastboot文件替换成随着aosp一起编译出来的即可,使用自行编译的fastboot即可。
1 2 3 rm ~/Android/Sdk/platform-tools/fastboot cp fastboot810r1 fastboot fastboot --version
通过wifi连接adb可实现群控adb -s 192.168.0.104:5555 install com.ttxapps.wifiadb_2.1.3-810031745_minAPI15(nodpi)_apkmirror.com.apk 安装apk
adb connect 192.168.0.104:5555 使用adb连接手机,如果异常“由于目标计算机积极拒绝,无法连接。 (10061)
1 2 3 4 5 adb root adb remount adb shell setprop service.adb.tcp.port 5555 adb tcpip 5555 adb connect 192.168.3.88
termux
adb -s 192.168.0.104:5555 install com.termux_92.apk adb被禁时在app端使用命令行操作
pkg update && pkg install htop 在app端安装管理进程的包
xdebuggable && XAppDebugxdebuggable 和XAppDebug模块并安装开启debug apk(需要借助ssr科学上网)
ro.debuggable
adb push MagiskHidePropsConf-v5.3.4.zip /sdcard/Download 并通过Magisk Manager-模块-下载-安装MagiskHidePropsConf-v5.3.4.zip
reboot-adb shell-props
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 1 - Edit device fingerprint 2 - Force BASIC key attestation 3 - Device simulation (disabled) 4 - Edit MagiskHide props 5 - Add/edit custom props 6 - Delete prop values 7 - Script settings 8 - Collect logs u - Perform module update check r - Reset all options/settings b - Reboot device e - Exit See the module readme or the support thread @ XDA for details. Enter your desired option: 4 1 - ro.debuggable 2 - ro.secure 3 - ro.build.type 4 - ro.build.tags 5 - ro.bootmode 6 - ro.boot.mode a - Change all props b - Go back to main menu e - Exit Pick several options at once by separating inputs with a comma. Example: 1,3,4 See the module readme or the support thread @ XDA for details. Enter your desired option: 1 You currently have the safe value set. Are you sure you want to change it to 1? Enter y(es), n(o) or e(xit): y Do you want to reboot now (y/n)? Enter y(es), n(o) or e(xit): y
getprop ro.debuggable 即可查看1,开启全局可调式
Pixel XL lineageos ,twrp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 adb reboot bootloader fastboot boot twrp-3.4.0-0-marlin.img 进入twrp 「TWRP主界面」->「Wipe」->「Format Data」 输入yes 「Adavanced Wipe」-> 勾选「Dalvik / ART Cache」、「Cache」、「System」、「Data」、「Internal Storage」(切勿勾选到「Vendor」) -> 划过滑动条确认擦除 「TWRP主界面」->「Advanced」->「ADB Sideload」(划过滑条即可) 勾选双清 adb sideload lineage-17.1-20201028-nightly-marlin-signed.zip 重启 设置-关于手机-版本号-8次打开开发者选项 设置-系统-高级-开发者选项-Android 调试 adb install MagiskManager-v7.5.1.apk adb install EdXposedManager-4.5.7-45700-org.meowcat.edxposed.manager-release.apk adb push magisk-riru-v21.3.zip /sdcard/Download adb push MagiskHidePropsConf-v5.3.4.zip /sdcard/Download adb push EdXposed-SandHook-v0.4.6.2.4529.-release.zip /sdcard/Download adb reboot bootloader fastboot boot twrp-3.4.0-0-marlin.img 「TWRP主界面」->「Advanced」->「ADB Sideload」(划过滑条即可) adb sideload Magisk-v20.4.zip 重启 通过Magisk模块新增选择下载目录,安装riru,MagiskHidePropsConf,EdXposed adb install JustTrustMePlus-debug.apk
marlin ,SR5-SuperSU-v2.82-SR5-20171001224502.zip,xposed-v89-sdk25-arm64.zip ,XposedInstaller_3.1.5
1 2 3 4 5 6 7 8 adb reboot bootloader ./flash-all.bat 设置-关于手机-版本号-8次打开开发者选项 设置-系统-高级-开发者选项-Android 调试 adb install XposedInstaller_3.1.5.apk fastboot boot twrp-3.4.0-0-marlin.img install SR5-SuperSU-v2.82-SR5-20171001224502.zip,xposed-v89-sdk25-arm64.zip adb push timeadjust.sh /data/local/tmp && sh timeadjust.sh
pixel系列安装xposed不可使用xposed-v89-sdk25-arm64.zip,只能ssr后谷歌下载xposed框架安装。
Nexus 6P 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 adb reboot bootloader fastboot devices fastboot erase cache 如出现< waiting for any device >,插拔usb fastboot erase userdata fastboot flashing unlock fastboot flash bootloader .\bootloader-angler-angler-03.68.img fastboot reboot-bootloader fastboot flash radio .\radio-angler-angler-03.81.img fastboot reboot-bootloader fastboot flash vendor .\image-angler-n2g48c\vendor.img fastboot reboot-bootloader fastboot flash system .\image-angler-n2g48c\system.img fastboot flash boot .\image-angler-n2g48c\boot.img fastboot flash recovery recovery.img fastboot erase cache fastboot erase userdata fastboot flash cache cache.img fastboot flash userdata userdata.img fastboot flashing lock
设置-关于手机-版本号8下点击-进入开发者模式-打开开发者选项
adb push UPDATE-SuperSU-v2.79-20161211114519.zip /sdcard
adb push xposed-v89-sdk25-arm64.zip /sdcard
rom:https://dl.google.com/dl/android/aosp/angler-n2g48c-factory-6a21e528.zip
解压得到angler-n2g48c-factory-6a21e528\angler-n2g48c\image-angler-n2g48c
superSu:https://download.chainfire.eu/1016/SuperSU/UPDATE-SuperSU-v2.79-20161211114519.zip
xposed安卓7.1对应sdk:https://dl-xda.xposed.info/framework/sdk25/arm64/xposed-v89-sdk25-arm64.zip
xposed apk:https://dl.xda-cdn.com/4/3/9/3/0/8/2/XposedInstaller_3.1.5.apk?key=4Rkip9MZy_4KitcodXSxBw&ts=1598862686
twrp:https://dl.twrp.me/angler/twrp-3.4.0-0-angler.img
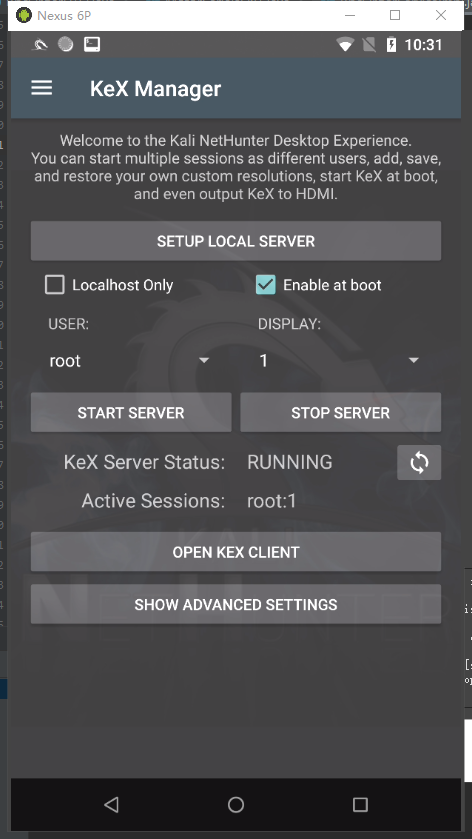
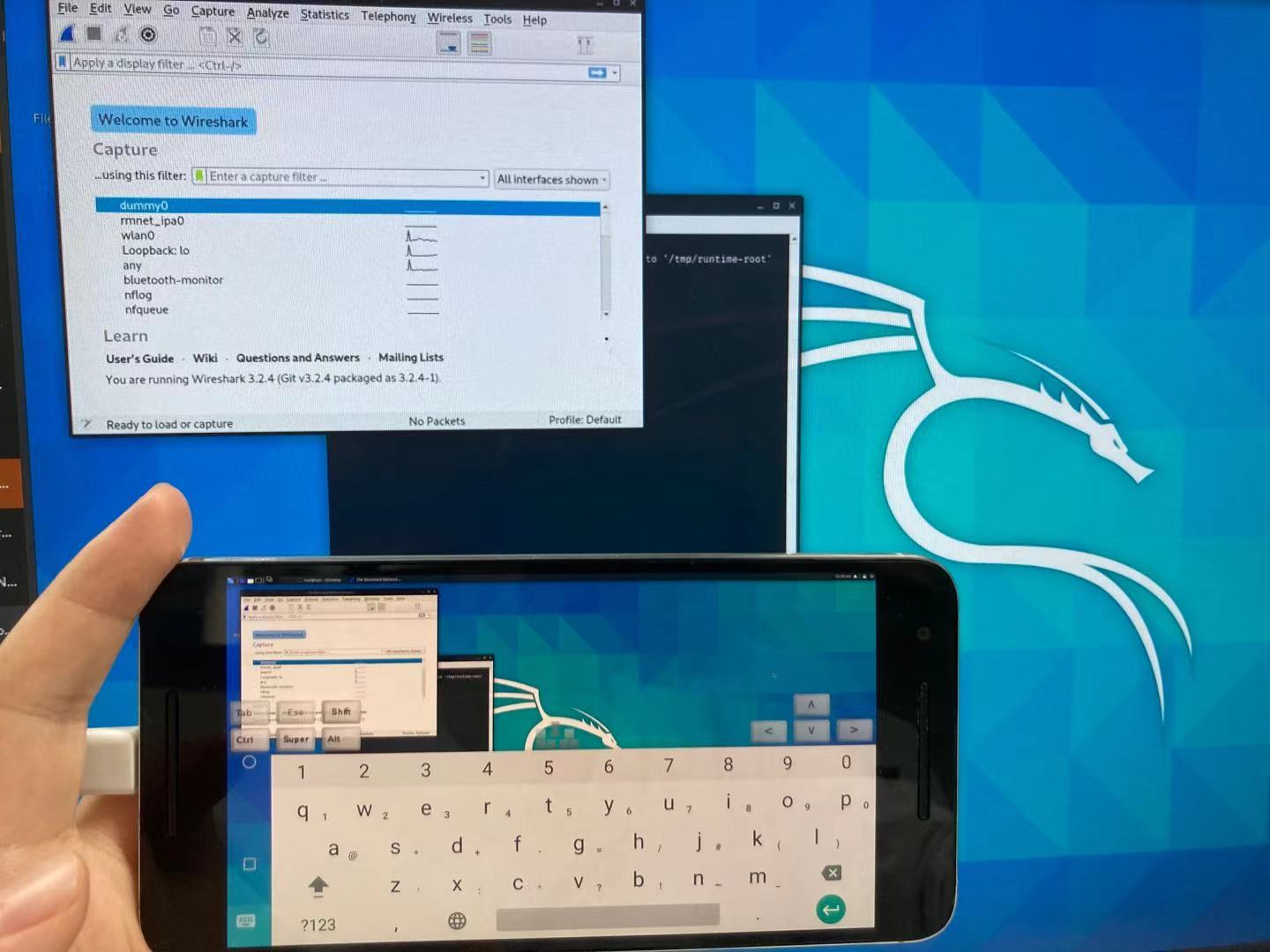
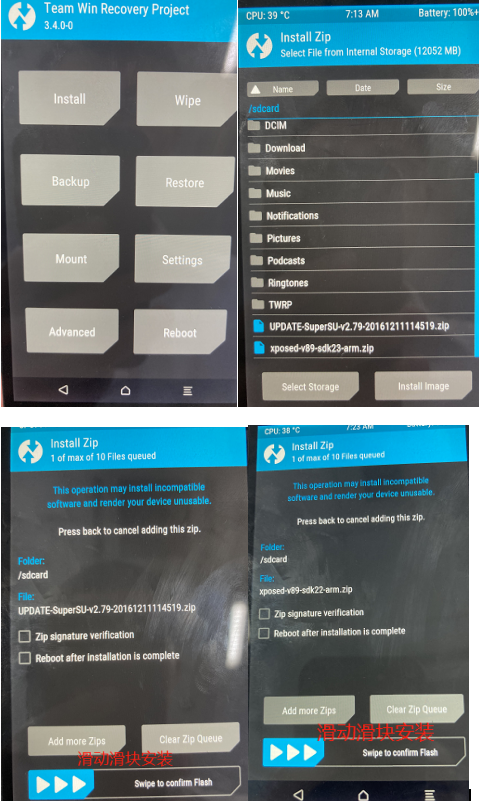
Kali NetHunter 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 wget https://dl.google.com/dl/android/aosp/angler-opm1.171019.011-factory-39448337.zip adb kill-server adb start-server adb reboot bootloader ./flash-all.sh 如报错替换fastboot,which fastboot,使用fastboot8.1.0r1,开启开发者选项,打开USB调试 https://www.kali.org/kali-nethunter/ https://www.offensive-security.com/kali-linux-nethunter-download/ Nexus 6P Oreo (ZIP) adb push SR5-SuperSU-v2.82-SR5-20171001224502.zip /sdcard/ adb push nethunter-2021.1-angler-oreo-kalifs-full.zip /sdcard/ adb push timeadjust.sh /sdcard/ adb reboot bootloader fastboot flash recovery twrp-3.4.0-0-angler.img 刷完之后按音量向下键,选择Recovery mode,按电源键进入, 进入Recovery之后,选择Install→SR5-SuperSU-v2.82-SR5-20171001224502.zip开始刷机。 再次进入recovery,把nethunter-2020.2-pre3-angler-oreo-kalifs-full.zip.torrent刷进去,中间解压Kali rootfs的过程,会至多25分钟 连接wifi sh timeadjust.sh 同步时间,reboot 刷机结束后进入系统首次也要先点击Nethunter的应用,申请的所有权限都给,左侧导航进入Kali Chroot Manager,点击START KALI CHROOT,只要初始化这一次,后续无论如何重启都会出现如图所示的Everything is fine and Chroot has been started!。 点开Nethunter终端这款App,选择KALI,进入Kali系统 apt update升级系统中的软件库信息 apt install neofetch htop jnettop 点开Nethunter进入标左侧签KeX Manager,点击“SETUP LOCAL SERVER”,会要求输入一个连接密码和显示密码,输入和确认即可,然后点击“START SERVER”开启服务器。点开“Nethunter KeX”这个App,在密码那一栏输入密码之后,点击“Connect”进行连接,即可直接进入Kali Nethunter操作系统的桌面。
搭配QtScrcpy就可以在电脑上观看手机屏幕上的内容,或者通过usb一拖四实现鼠标键盘完全电脑操作。该系统自动集成了java,BurpSuite2020.06,charles,python3,python。
vnc 点开Nethunter这个app
切换到Kali Chroot Manager,START KALI CHROOT 切换到Kali Services,将SSH启动并且勾选Start at Boot,这样就拥有了sshd 切换到Kex Manage–SETUP LOCAL SERVER 设置好密码后–取消Localhost Only–START SERVER–OPEN KEX CLIENT
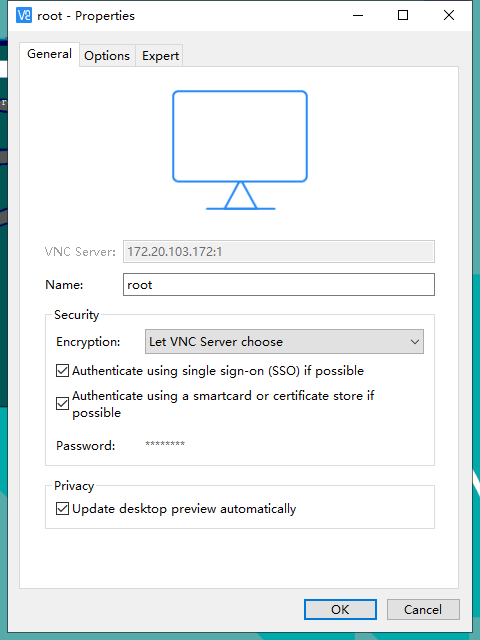
打开VNC Viewer,通过NetHunter 终端查看ip地址,显示器为1,开启VNC登录
通过一拖四的typec转USB,连接键盘鼠标,将Nexus 6p变成一台kali电脑。
Nexus 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 adb reboot bootloader fastboot oem unlock fastboot erase cache 如出现< waiting for any device >,插拔usb fastboot erase userdata fastboot flash bootloader .\bootloader-hammerhead-hhz20h.img fastboot flash radio .\radio-hammerhead-m8974a-2.0.50.2.30.img fastboot reboot-bootloader cd .\image-hammerhead-m4b30z\ fastboot flash recovery recovery.img fastboot flash boot boot.img fastboot flash system system.img fastboot flash userdata userdata.img fastboot erase cache fastboot erase userdata fastboot flash cache cache.img fastboot flash userdata userdata.img fastboot reboot
设置-关于手机-版本号8下点击-进入开发者模式-打开开发者选项
adb push UPDATE-SuperSU-v2.79-20161211114519.zip /sdcard
adb push .\xposed-v89-sdk23-arm.zip /sdcard
1 2 3 4 5 6 7 adb reboot bootloader fastboot flash recovery twrp-3.4.0-0-hammerhead.img 然后进入recovery mode adb install .\XposedInstaller_3.1.5.apk 安装Xposed adb shell adb shell 输入su获取超级用户权限 chmod 711 /data/user/0/de.robv.android.xposed.installer reboot 安装完毕
小米 Mix 2 打开开发者选项-usb调试
adb reboot bootloader 解锁bootloader,执行miflash_unlock.exe
EdXposed-SandHook-v0.4.6.2.4529.-release.zip
twrp-3.3.1-1-chiron.img
1 2 3 4 5 6 7 8 9 10 11 12 13 adb reboot bootloader fastboot flash recovery twrp-3.3.1-1-chiron.img fastboot boot twrp-3.3.1-1-chiron.img adb push lineage-17.0-chiron.zip 不能有中文 进入twrp后清除Cache,System,Data分区 install lineage-17.0-chiron.zip install Magisk-v20.4.zip adb install MagiskManager-v7.5.1.apk adb install EdXposedManager-4.5.7-45700-org.meowcat.edxposed.manager-release.apk 在magisk中安装 adb push magisk-riru-v21.3.zip /sdcard/Download adb push MagiskHidePropsConf-v5.3.4.zip /sdcard/Download adb push EdXposed-SandHook-v0.4.6.2.4529.-release.zip /sdcard/Download
小米6 我的设备-全部参数-双击8次MIUI版本-开发者选项
更多设置-开发者选项-usb调试
解锁bootloader,执行miflash_unlock.exe
https://download.lineageos.org/sagit lineage-17.1-20201022-nightly-sagit-signed.zip
twrp-3.3.1-2-sagit.img
fw_sagit_miui_MI6Global_V10.4.1.0.PCAMIXM_38edd1584c_9.0.zip
1 2 3 4 5 6 7 8 9 10 11 12 13 adb reboot bootloader 重启到引导系统 fastboot flash recovery twrp-3.3.1-2-sagit.img fastboot reboot 执行完命令马上长按音量+ 清除数据 fastboot reboot 重启进入 TWRP ,执行完命令马上长按音量+,滑动开始 「TWRP主界面」->「Wipe」->「Format Data」 输入yes 「Adavanced Wipe」-> 勾选「Dalvik / ART Cache」、「Cache」、「System」、「Data」、「Internal Storage」(切勿勾选到「Vendor」) -> 划过滑动条确认擦除 「TWRP主界面」->「Advanced」->「ADB Sideload」(划过滑条即可) adb sideload fw_sagit_miui_MI6Global_V10.4.1.0.PCAMIXM_38edd1584c_9.0.zip 刷完后手机会自动退出 ADB Sideload 「TWRP主界面」->「Advanced」->「ADB Sideload」(划过滑条即可) adb sideload lineage-17.1-20201105-nightly-sagit-signed.zip 刷完后手机会自动退出 ADB Sideload 重启按住音量+ 进入twrp install Magisk-v20.4.zip 重启 adb install MagiskManager-v7.5.1.apk
设置-关于手机-版本号-8次打开开发者选项
设置-系统-高级-开发者选项-Android 调试
1 2 3 4 5 6 adb install EdXposedManager-4.5.7-45700-org.meowcat.edxposed.manager-release.apk 在magisk中安装 adb push magisk-riru-v21.3.zip /sdcard/Download adb push MagiskHidePropsConf-v5.3.4.zip /sdcard/Download adb push EdXposed-SandHook-v0.4.6.2.4529.-release.zip /sdcard/Download adb install JustTrustMePlus-debug.apk
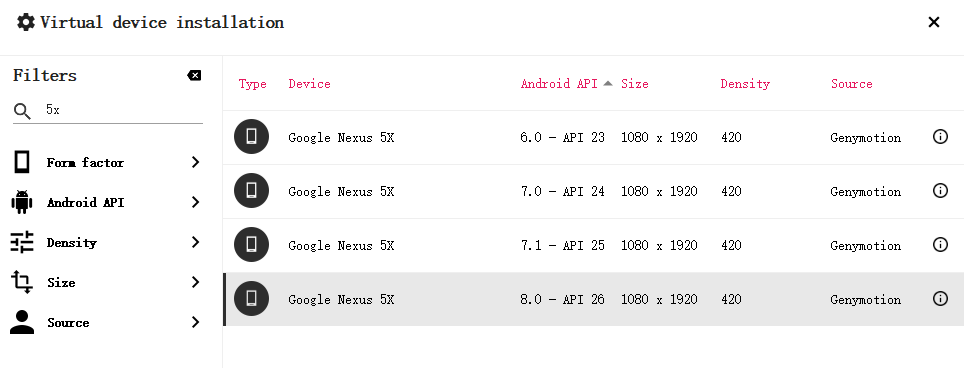
安装全程开全局代理,安装nexus 5x 8.0
adb 无法连接genymotion怎么办?
修改genymotion的settings,Use custom Android SDK tools为本地android sdk路径
arm桥接
uname -a i686 查看cpu架构为x86 32位 不支持arm,需要安装arm桥 ,直接将 Genymotion-ARM-Translation_for_8.0.zip拖入nexus 5x 8.0, 进行安装
Kali 别用Windows了,鲁迅曾经说过,他在逆向生涯中超过一半的苦难均由Windows赐予 。
vmware安装文件 秘钥:YC34H-6WWDK-085MQ-JYPNX-NZRA2
kali-linux-2020.4-vmware-amd64.7z种子 ,使用vmware打开vmx文件,配置6g内存,80g磁盘存储,网络适配选择桥接到本地网卡(虚拟网络编辑器),默认账密:kali/kali,sudo passwd root 修改密码123456
重启后使用root登录,android-studio-ide-201.7042882-linux.tar.gz安装包
基本配置 1 2 3 4 5 6 7 8 apt update;apt install htop jnettop tmux iotop dpkg-reconfigure tzdata 选择Asia-Shanghai apt update 更新自动同步时间 apt install xfonts-intl-chinese 装中文字体 apt-get install ttf-wqy-microhei # nano /etc/ssh/sshd_config 开启sshd PermitRootLogin yes # /etc/init.d/ssh start
常用软件 1 2 3 4 5 6 7 tar zxf android-studio-ide-201.7042882-linux.tar.gz cd ~/Desktop/android-studio/bin && ./studio.sh 启动android studio ctrl+shift+t 当前窗口新建终端 vim ~/.zshrc export PATH="/root/Android/Sdk/platform-tools:$PATH" 加入环境变量 exec "$SHELL" dpkg -i code_1.52.1-1608136922_amd64.deb 安装vscode
as若报错To build this project, accept the SDK license agreements and install the missing components?
执行/root/Android/Sdk/tools/bin/sdkmanager –licenses
Android设备投屏
NodeJs
jadx-1.2.0.zip 多dex打开,修改jadx-gui中set DEFAULT_JVM_OPTS="-Xms512M" "-Xmx8g",加入zshrc的环境变量中export PATH="/root/Android/Sdk/ndk-bundle:/root/Android/Sdk/platform-tools:${JAVA_HOME}/bin:$PATH:/root/Desktop/charles/bin:/root/Desktop/jadx-1.2.0/bin:$NDK_HOME"
1 2 3 curl -fsSL https://deb.nodesource.com/setup_14.x | bash - apt-get install -y nodejs npm install --save @types/frida-gum frida代码提示
jeb-pro-3.19.1.202005071620_pwd_ilbtcdnwiuypbzeo_.7z 运行./jeb_linux.sh,输入密码:ilbtcdnwiuypbzeo,进入界面点击Manual Key Generation中间按钮获取LICENSE DATA,运行jebKeygen.py 获取license key后输入到界面的key中,continue
Kali Linux里的as4的DDMS启动失败,原因是要用as自带的jre来启动,直接./monitor用的是Kali系统的jdk,版本太高了ln -s /root/Desktop/android-studio/jre/ /root/Android/Sdk/tools/lib/monitor-x86_64/,然后通过~/Android/Sdk/tools/monitor打开ddms
vim ~/.bashrc && source ~/.bashrc
export PATH=$PATH:/root/Android/Sdk/platform-tools
jdk1.8
1 2 3 4 5 6 7 8 9 10 11 12 apt-get remove openjdk-11-jre-headless:amd64 apt-get remove openjdk-11-jre:amd64 tar zxf jdk-8u191-linux-x64.tar.gz -C /opt/jdk vim ~/.zshrc export JAVA_HOME=/opt/jdk export CLASSPATH=.:${JAVA_HOME}/lib export PATH="/root/Android/Sdk/ndk-bundle:/root/Android/Sdk/platform-tools:${JAVA_HOME}/bin:$PATH" source ~/.zshrc update-alternatives --install /usr/bin/java java /opt/jdk/bin/java 1 update-alternatives --install /usr/bin/javac javac /opt/jdk/bin/javac 1 update-alternatives --set java /opt/jdk/bin/java update-alternatives --set javac /opt/jdk/bin/javac
nexus 5x
安装流程 twrp->SuperSu-> nethunter
kali nethunter 下载nexus 5x nethunter ,使用投屏可变成一个迷你的linux渗透系统,通过twrp进行install ,sh userinit.sh 同步时间
tab smali与java代码转换 ctrl+b 下断点(注意这个必须在smali代码界面才有用) esc 回退上一级引用
activity_main.xml中配置的view组件:jeb中以十六进制存在于代码中,利用计算器的程序员模式转为十进制,jadx将该十进制存入resources.arsc,gda有APK入口直接进入MainActivity,同样以十六进制存入代码中。
科学上网 dpkg -i electron-ssr-0.2.6.deb 卸载使用-r,查询使用-l ,失败缺少包,经过https://pkgs.org/ 查找所缺的包并安装
1 2 3 4 5 6 apt --fix-broken install apt-get install gconf2 dpkg -i libdbusmenu-gtk4_18.10.20180917_bzr492+repack1-2_amd64.deb dpkg -i libindicator7_0.5.0-4_amd64.deb dpkg -i libappindicator1_0.4.92-8_amd64.deb dpkg -i electron-ssr-0.2.6.deb
启动electron-ssr的pac模式即可
基本命令 getprop ro.product.cpu.abi 判断系统cpu版本 虚拟机一般都是x86 dumpsys meminfo pid 查看进程占用内存映射的信息 cat /proc/pid/maps 进程加载的so cat /proc/pid/maps | grep -i libart.so 所有java代码通过libart.so解析,脱壳机的关键 dumpsys activity top 显示当前的Activity,显示View Hierarchy,看view的类信息 dumpsys package com.soviet.hook4crawler 查看运行包信息 pm list packages 查看所有安装的包
pyenv环境 对python不同包(frida,objection…)多版本管理
全套安装最新版本:proxychains pip install objection
3.8.5 1 2 3 4 5 6 7 8 9 10 11 12 13 ctrl+alt+t 新建终端 git clone https://github.com/pyenv/pyenv.git ~/.pyenv 安装pyenv,python全版本随意切 echo 'export PYENV_ROOT="$HOME/.pyenv"' >> ~/.zshrc echo 'export PATH="$PYENV_ROOT/bin:$PATH"' >> ~/.zshrc echo -e 'if command -v pyenv 1>/dev/null 2>&1; then\n eval "$(pyenv init -)"\nfi' >> ~/.zshrc exec "$SHELL" apt-get update; apt-get install --no-install-recommends make build-essential libssl-dev zlib1g-dev libbz2-dev libreadline-dev libsqlite3-dev wget curl llvm libncurses5-dev xz-utils tk-dev libxml2-dev libxmlsec1-dev libffi-dev liblzma-dev PYTHON_CONFIGURE_OPTS="--disable-ipv6" proxychains4 pyenv install 3.8.5 使用代理访问,不然会报错you can specify "--disable-ipv6". pyenv local 3.8.5 python -V pyenv local system 切换原系统pyenv pip install frida-tools proxychains4 pip install objection==1.9.5
针对指定frida版本的objection,通过pypi 中查找frida release日期稍后一点版本的objection即可frida-server-14.2.8-android-arm64.xz
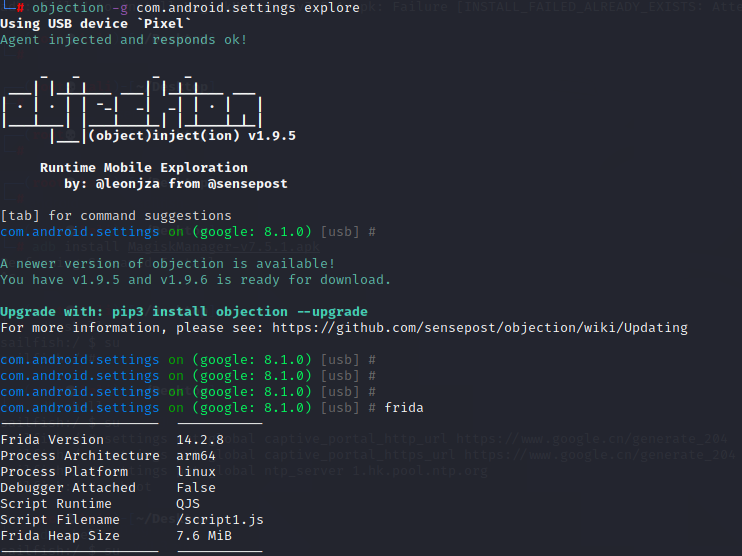
1 2 3 4 5 6 adb push frida-server-14.2.8-android-arm64 /data/local/tmp mv frida-server-14.2.8-android-arm64 fs1428arm64 改名fs1428arm64,防止反调试 chmod 777 fs1428arm64 加权 ./fs1428arm64 frida-ps -U android hooking list classes
1 2 3 4 5 6 7 8 9 10 11 12 13 14 android sslpinning disable 关闭app的ssl校验 android hooking set return_value com.xxx.xxx.methodName false 设置返回值 android hooking generate simple com.sf.security.AuthConfig 直接生成hook代码 android hooking search classes [search_name] android hooking search methods [search_name] android intent launch_activity [class_activity] android hooking list class_methods com.android.settings.DisplaySettings 查看类全部方法 android root disable 关闭app的root检测 android heap search instances com.android.settings.DisplaySettings 堆内存中搜索指定类的实例 android heap execute 40977078 c 拿到hashcode调用c方法 android heap execute 0x2526 getPreferenceScreenResId 直接调用指定实例下的方法 plugin wallbreaker classdump --fullname com.sf.security.AuthConfig plugin wallbreaker objectsearch com.sf.security.AuthConfig plugin wallbreaker objectdump --fullname 0x36d6 查看源码
3.8.0 1 2 3 4 5 6 PYTHON_CONFIGURE_OPTS="--disable-ipv6" proxychains4 pyenv install 3.8.0 pyenv local 3.8.0 PYTHON_CONFIGURE_OPTS="--disable-ipv6" proxychains4 pip install frida==12.8.0 PYTHON_CONFIGURE_OPTS="--disable-ipv6" proxychains4 pip install frida-tools==5.3.0 PYTHON_CONFIGURE_OPTS="--disable-ipv6" proxychains4 pip install objection==1.8.4 objection -g com.android.settings explore
7z x frida-server-12.8.0-android-arm64
1 2 3 4 5 adb push frida-server-12.8.0-android-arm64 /data/local/tmp mv frida-server-12.8.0-android-arm64 fs128arm64 改名防止反调试 chmod 777 frida-server-12.8.0-android-arm64 objection -g com.android.settings explore android hooking list classes
特定版本frida
按照这个顺序,在装objection的时候,就会直接Requirement already satisfied,不会再去下载新的frida来安装了。
1 2 3 pip install frida==12.8.0 pip install frida-tools==5.3.0 pip install objection==1.8.4
frida开发环境
pyenv local 3.8.0 && ./fs128arm64
git clone https://github.com/oleavr/frida-agent-example.git cd frida-agent-example/ npm install 使用VSCode等IDE打开此工程,在agent下编写typescript,会有智能提示。 npm run watch会监控代码修改自动编译生成js文件 frida -UF -l demo.js usb连接手机保存将自动调用demo.js 进行hook Java.perform(function(){console.log("frida hook")}) frida -UF -l demo.js –runtime=v8 使用v8引擎 Java.perform(()=>{console.log("Hello World")}) frida-ps -U 查看所有进程 frida -H 192.168.0.100:5555 -f com.ttxapps.wifiadb -l demo.js –runtime=v8 远程hook,-l指定脚本 frida -Uf com.android.settings -l demo.js –runtime=v8 –no-pause 经过usb主动启动应用调用demo.js,-f是spawn模式,–no-pause直接加载应用,没有的话需要%resume启动主线程 frida -UF –runtime=v8 -e “Java.perform(()=>{console.log(‘Hello World’)})” -o /root/log.txt 直接执行脚本写入文件 远程连接
./fs128arm64 -v -l 0.0.0.0:8888 指定端口启动frida,默认端口27042
frida-ps -H 192.168.0.8:8888 指定-U表示usb,-H表示主机ip
frida -H 192.168.0.8:8888 -F 指定-H表示主机ip,-F表示前台应用,输入frida即可查看Frida信息
cd frida-agent-example / && npm install && npm run watch && frida -H 192.168.0.8:8888 -F -l agent/demo.js 远程调用js脚本
1 2 3 4 5 6 7 Java.perform(()=>{console.log("Hello World")}) function main(){ Java.perform(function(){ console.log("hello") }) } setImmediate(main)
远程调用
1 2 3 4 5 6 7 8 9 10 11 12 13 import frida device = frida.get_usb_device() print(device.get_frontmost_application()) #pid = device.spawn(["com.onejane.demo02"]) pid=device.get_frontmost_application().pid # 若双进程保护,指定pid进行hook print(device.enumerate_processes()) # 枚举所有进程 print(device.enumerate_applications()) # 枚举所有包名 # device.resume(pid) # time.sleep(1) session = device.attach(pid) with open("demo.js") as f: script = session.create_script(f.read()) script.load()
plugins
1 2 3 4 proxychains git clone https://github.com/hluwa/FRIDA-DEXDump ~/Downloads/FRIDA-DEXDump 脱壳 mv ~/Downloads/FRIDA-DEXDump/frida_dexdump ~/.objection/plugins/dexdump 在plugins子目录插件下必须有__init__.py proxychains git clone https://github.com/hluwa/Wallbreaker ~/.objection/plugins/Wallbreaker 内存漫游 objection -N -h 192.168.0.8 -p 8888 -g com.android.settings explore -P ~/.objection/plugins 远程连接批量加载插件
卸载 pip uninstall frida
pip uninstall frida-tools
pip uninstall objection
pixel+android10
下载marlin-qp1a.191005.007.a3-factory-bef66533.zip ,将aosp10r2_marlin线刷包修改其中android-info.txt压缩为image-marlin-qp1a.191005.007.a3.zip
1 2 3 4 5 require board=marlin|sailfish require version-bootloader=8996-012001-1908071822 require version-baseband=8996-130361-1905270421
刷机完成后安装**MikManager **,参考Xposed搭建开发里安装LSPosed,无线网如果有问题,安装captivemgr申请权限如果su冲突关闭magisk中的超级用户访问权限。配置frida-server-15.1.11-android-arm64.xz 和frida-server-14.2.18-android-arm64.xz 所需要的的环境
1 2 3 4 5 6 7 8 9 10 11 PYTHON_CONFIGURE_OPTS="--disable-ipv6" proxychains4 pyenv install 3.8.6 pyenv local 3.8.6 PYTHON_CONFIGURE_OPTS="--disable-ipv6" proxychains4 pip install frida==14.2.18 PYTHON_CONFIGURE_OPTS="--disable-ipv6" proxychains4 pip install frida-tools==9.2.4 PYTHON_CONFIGURE_OPTS="--disable-ipv6" proxychains4 pip install objection==1.11.0 PYTHON_CONFIGURE_OPTS="--disable-ipv6" proxychains4 pyenv install 3.8.7 pyenv local 3.8.7 PYTHON_CONFIGURE_OPTS="--disable-ipv6" proxychains4 pip install frida==15.1.11 PYTHON_CONFIGURE_OPTS="--disable-ipv6" proxychains4 pip install frida-tools==10.4.1 PYTHON_CONFIGURE_OPTS="--disable-ipv6" proxychains4 pip install objection==1.11.0
辅助-选择脚本,启动后根据logcat查看app启动时log
1 2 3 4 5 6 7 8 9 10 function Log(info){ Java.perform(function(){ var LogClass = Java.use("android.util.Log"); LogClass.e("mikrom",info); }) } function main() { Log("666") } setImmediate(main)
辅助-监听,frida attach模式,启动app后再附加
辅助-监听并阻塞,frida spawn模式,启动app后阻塞启动hook