篇幅有限
完整内容及源码关注公众号:ReverseCode,发送 冲
Socket
所有的应用层都逃不掉底层用Socket来传输,只要掌握了Socket,对上层应用就是降维打击。
新建HttpSocket项目,并在AndroidManifest.xml配置网络权限<uses-permission android:name="android.permission.INTERNET" />
1 | public class MainActivity extends AppCompatActivity { |
关键类定位
objection -g com.onejane.httpsocket explore
android heap search instances java.net.Socket 查看堆内存中是否有该实例
android hooking search classes Socket 搜索与Socket相关的类
android hooking watch class java.net.Socket 默认hook类的所有方法没有构造函数
android hooking watch class_method java.net.Socket.$init –dump-args –dump-backtrace –dump-return 手动调用hook构造函数
vim ~/.pyenv/versions/3.8.0/lib/python3.8/site-packages/objection/agent.js 输入:9211跳转到9211行,加上.concat([“$init”]),会影响objection的稳定性
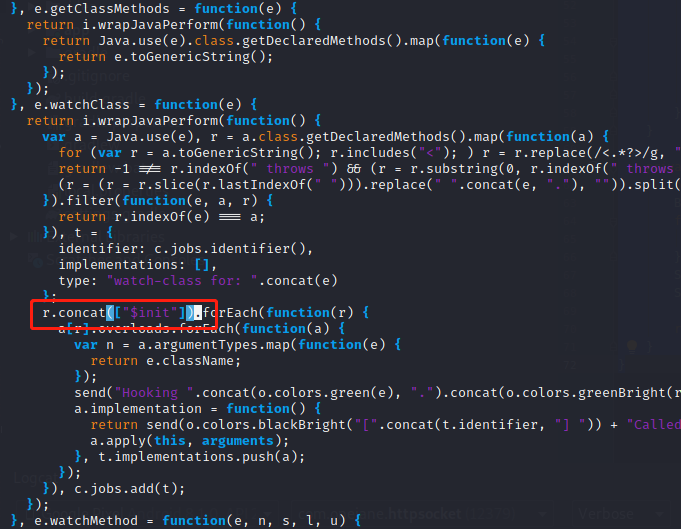
将与Socket相关的类添加前缀android hooking watch class存入socket.txt
objection -g com.onejane.httpsocket explore -c ~/Desktop/socket.txt 批量hook,如果崩掉,需要将崩掉的类从文本中移除
okhttp底层走的socket
android hooking watch class_method java.net.AbstractPlainSocketImpl.acquireFD --dump-args --dump-backtrace --dump-return
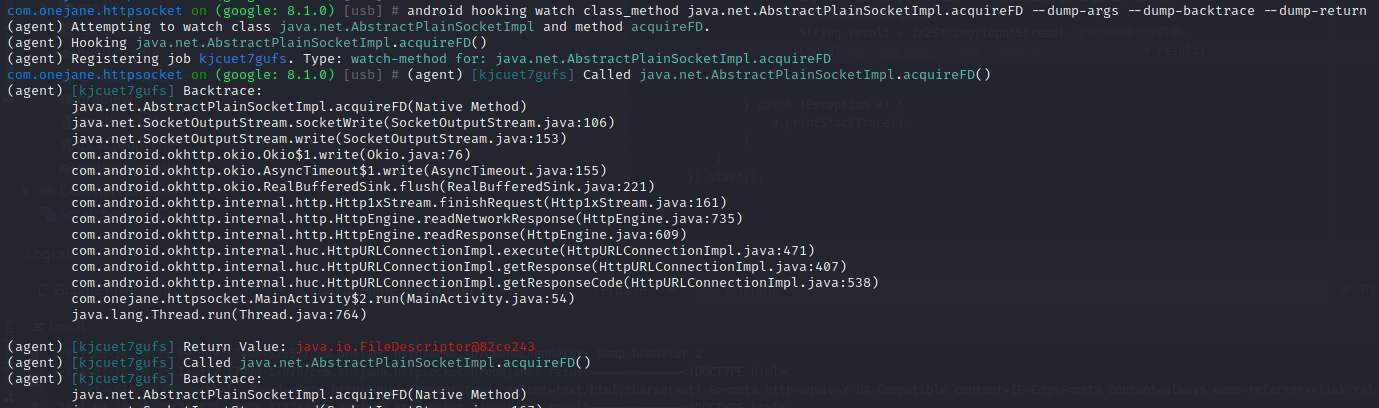
根据hook的结果拿到java.net.SocketOutputStream.write方法就是socket写入时调用的方法,针对该方法进行hook
android hooking watch class_method java.net.SocketOutputStream.write --dump-args --dump-backtrace --dump-return
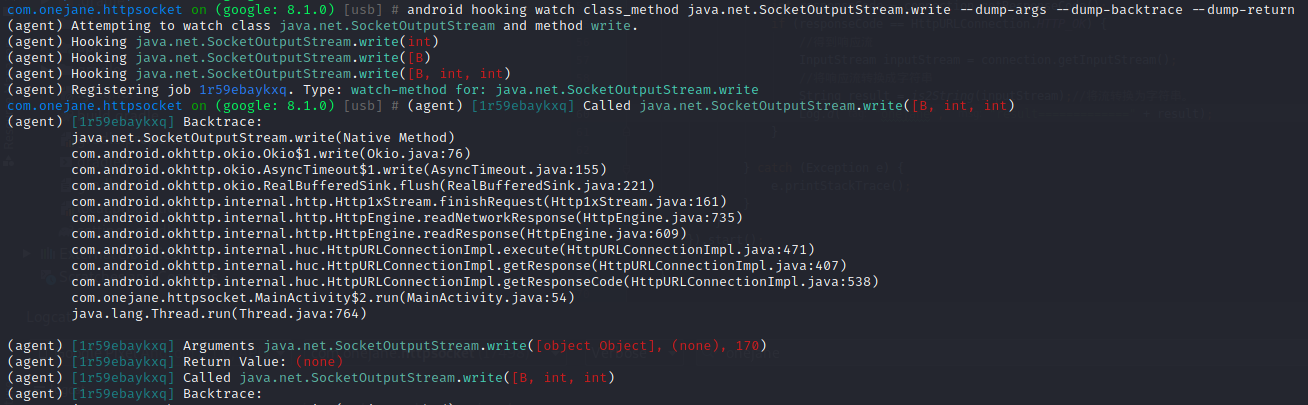
SocketInputStream.read的hook结果复制到010Editor,搜索1f8b,删除前面所有字符,保存为gzip,解压查看结果就是百度网页结果
socket自吐
实现http与https的socket自吐,修改url地址http://www.baidu.com/为https://www.baidu.com/, 有这两个自吐,可以通杀所有协议层的收发包内容
1 | function hook_socket(){ |
frida -UF -l hookSocket.js 使用git clone https://github.com/peiniwan/Ganhuo.git 编译源码编译安装GanHuo.apk查看代码家栏,通过010Editor获取转换后的Unicode码,即为抓包结果
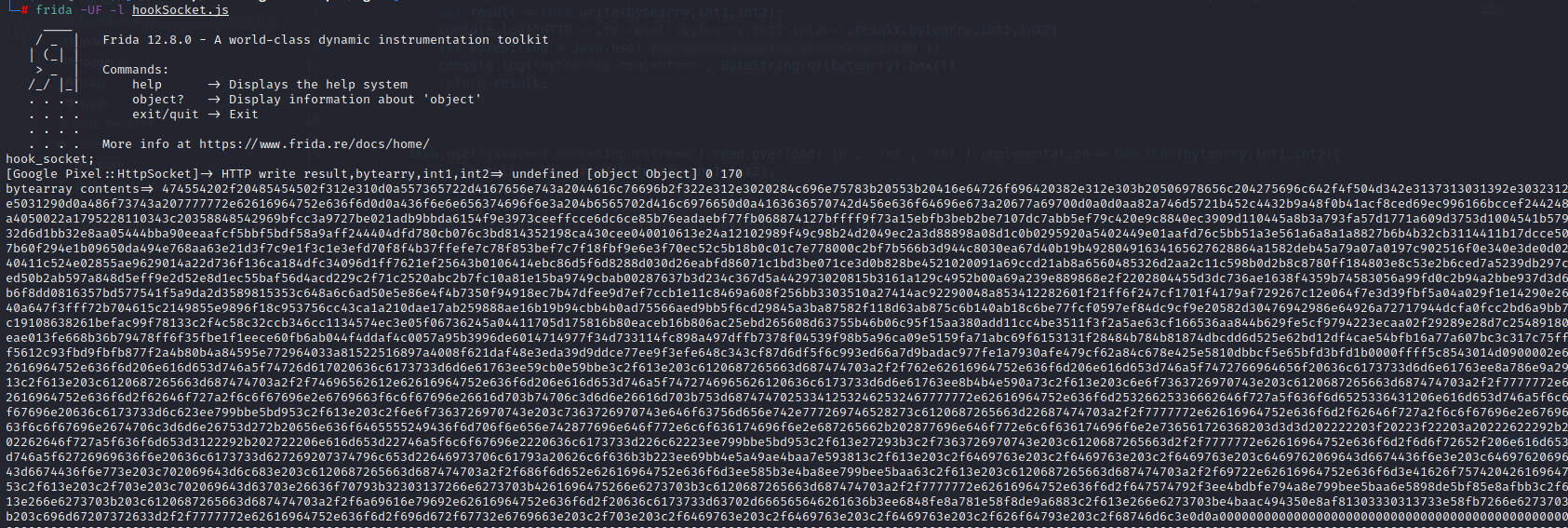
Websocket
虚拟机网卡切换为桥接模式:192.168.0.104
server
wget https://github.com/gotify/server/releases/download/v2.0.20/gotify-linux-amd64.zip
unzip gotify-linux-amd64.zip
chmod +x gotify-linux-amd64
./gotify-linux-amd64
client
adb install Gotify.apk
输入server地址http://192.168.0.104 admin/admin
cli
wget -O gotify https://github.com/gotify/cli/releases/download/v1.2.0/gotify-cli-linux-amd64
chmod +x gotify
mv gotify /usr/bin/gotify
gotify init
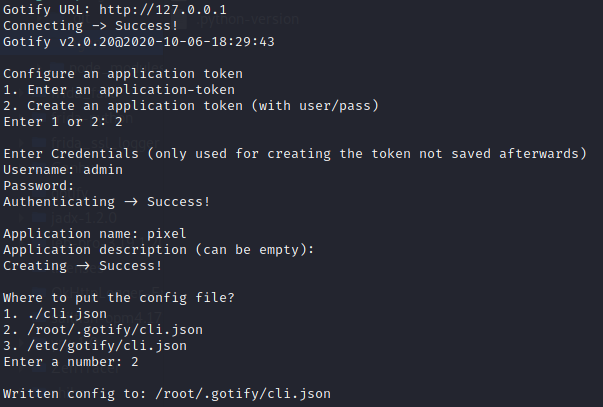
gotify push -t “my title” -p 10 “my message” 服务器向手机发送消息
hook_okhttp3_logging
添加十六进制转换,在控制台中以字符串显示
1 | function jhexdump(array) { |
使用console.log(jhexdump(bytearry))替换console.log(“bytearray contents=>”, ByteString.of(bytearry).hex())
frida -UF -l hookSocket.js 使用socket自吐依旧可以通杀抓包
pm list packages|grep -i gotify 获取包名
frida -U -f com.github.gotify -l hookSocket.js –no-pause -o gotify.log
objection -g com.github.gotify explore
android hooking search classes websocket 查找内存中和websocket相关的类很少,可以通过android hooking watch class * ,存入websocket.txt文件批量hook
1 | objection -g com.github.gotify explore -c ~/Desktop/gotify/websocket.txt |
android hooking search classes websocket 发现okhttp3.WebSocket,通过hook_okhttp3_logging脚本进行hook抓包frida -U -f com.github.gotify -l hookOkhttp3.js --no-pause,logcat|grep okhttpGET 查看可以抓到ok3的websocket包
android hooking search classes com.xabber.xmpp.smack 基于xmpp协议聊天软件xabber搜索包名并批量hook
android hooking watch class_method java.lang.String.toString –dump-args -dump-backtrace –dump-return
hookWebSocket
vim hookWebSocket.js 综合基于hook和枚举的方式抓包websocket
1 | function hook_okhttp3() { |
OkHttpLogger-Frida
frida -UF -l OkHttpLogger-Frida/okhttp_poker.js 抓包websocket
Protobuf
直播/弹幕协议Protobuf逆向分析,手把手教你使用ProtoBuf,通过gRPC服务在Android上进行网络请求
服务端
192.168.0.102
1 | systemctl stop firewalld.service |
客户端
192.168.0.104
git clone https://github.com/xuexiangjys/Protobuf-gRPC-Android.git ,其中helloworld.proto通过protoc编译生成HelloReply.java
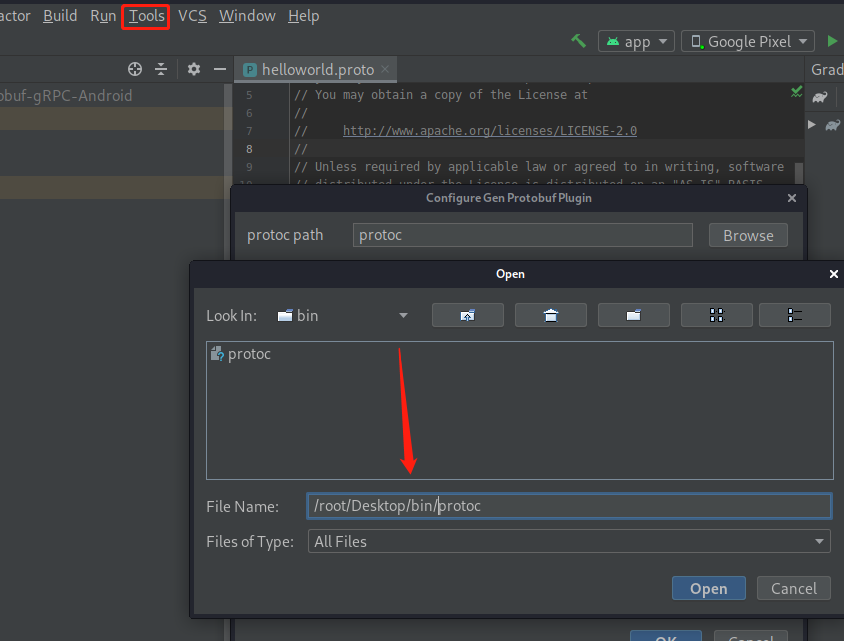
手动编译,idea中安装GenProtobuf将binary进行encode和decode
wget https://github.com/protocolbuffers/protobuf/releases/download/v3.13.0/protoc-3.13.0-linux-x86_64.zip
unzip protoc-3.13.0-linux-x86_64.zip
as-Tools-Configure GenProtobuf
右键hellooworld.proto点击quick gen protobuf here 实现手动编译,生成的编译代码使用了大量的google的protobuf基础库
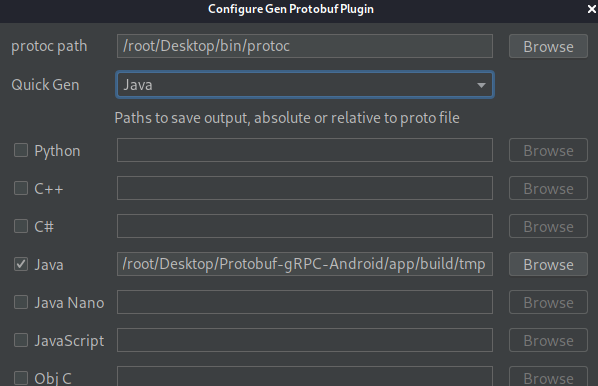
安装启动Protobuf-gRPC-Android,保证服务端和客户端互相ping通,可以通过nc 192.168.0.102 50052 给服务端发送数据,服务端使用nc -l 50052接收,如果互通消息就可以收到,否则使用NPS将服务端的50051端口服务映射到指定服务器ip的指定端口(需要在服务端安装nps客户端,在nps服务端配置该nps客户端)。
如果没有响应,ps -ef|grep protobuf 获取到进程id后,logcat|grep -i 22916 查看log,退出重进gRPC-普通请求按钮,输入服务端ip,端口及内容发送请求。
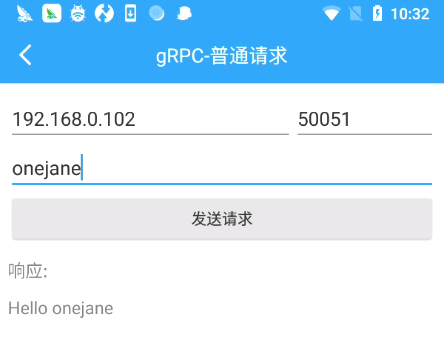
1 | adb shell |
关注打印出来的几个函数:
com.google.protobuf.WireFormat.makeTag
com.google.protobuf.CodedOutputStream$OutputStreamEncoder.write([B, int, int)
com.google.protobuf.CodedInputStream.readTag()
com.google.protobuf.WireFormat.getTagFieldNumber(int)
com.google.protobuf.Utf8.encode(java.lang.CharSequence, [B, int, int)
com.google.protobuf.CodedInputStream.newInstance([B, int, int, boolean)
1 | android hooking watch class_method com.google.protobuf.Utf8.encode --dump-args --dump-backtrace --dump-return |
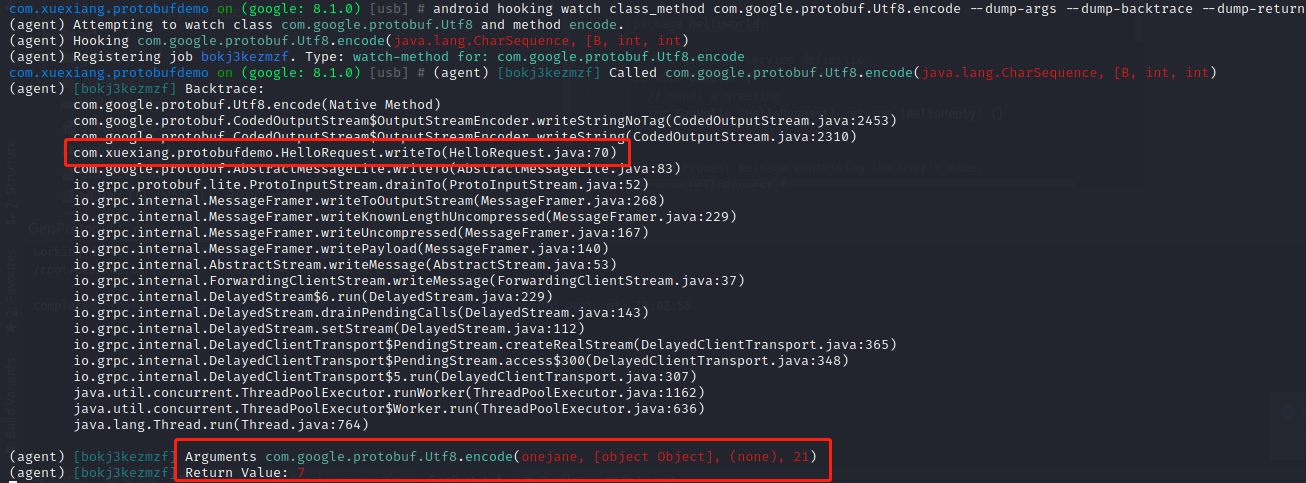
同理,makeTag的调用栈也是从用户代码中的writeTo调用而来。
frida -UF -l hookSocket.js -o protobuf.txt 通杀自吐打印出protubuf的包数据
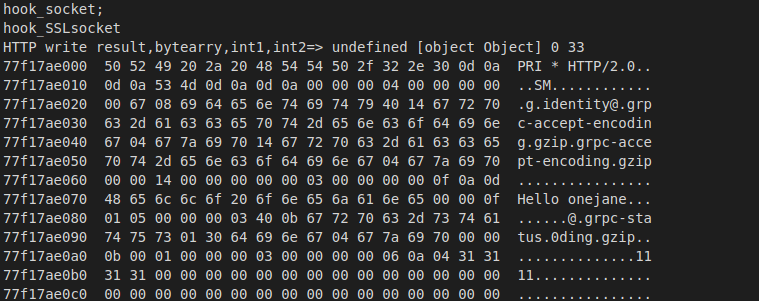
1 | plugin wallbreaker objectsearch com.xuexiang.protobufdemo.HelloReply |

