Kali
kali里面时间老是不对,其实只是时区不对而已,一个命令就搞定:
dpkg-reconfigure tzdata然后选择Asia→Shanghai,然后重启即可。
KaliLinux默认不带中文
apt install xfonts-intl-chinese
apt install ttf-wqy-microhei
kali装中文输入法,参考https://blog.csdn.net/qq_42333641/article/details/89325576
apt install htop 动态查看当前活跃占用高的进程。
apt install jnettop 流量查看工具。
wifiadb qtscrcpy wifi群控
安装pyenv https://github.com/pyenv/pyenv-installer
1 | sudo apt-get update; sudo apt-get install make build-essential libssl-dev zlib1g-dev \ |
安装vscode
dpkg -i code_1.45.1-1589445602_amd64.deb
安装node
1 | apt update |
刷机
1 | wget https://dl.google.com/dl/android/aosp/sailfish-opm1.171019.011-factory-56d15350.zip |
frida
1 | 1. git clone https://github.com/oleavr/frida-agent-example.git |
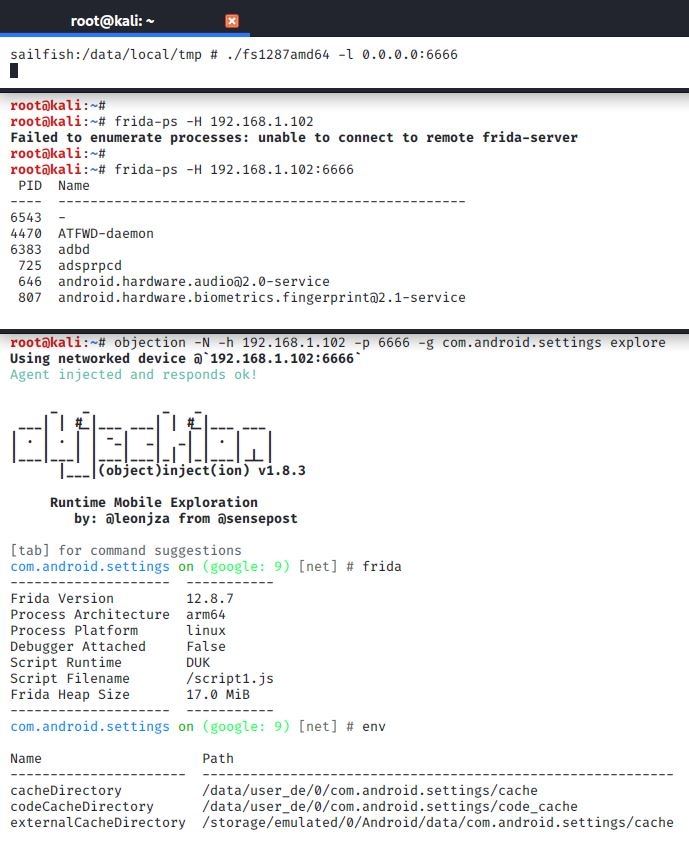
1 | android hooking list activities |
实用FRIDA进阶:内存漫游、hook anywhere、抓包
jadx-gui-1.3.5-no-jre-win.exe 反编译软件
java -jar abe-all.jar unpack 1.ab 1.tar 其中abe.jar 安卓备份文件
1 | wget https://redirector.gvt1.com/edgedl/android/studio/ide-zips/2021.1.1.23/android-studio-2021.1.1.23-linux.tar.gz |
frida -U com.example.lesson -l lesson.js
1 | function main(){ |
Frida
npm i -g @types/frida-gum 安装vs的frida自动提示
frida_example_1.0
frida -U -f com.frida.example -l hook.js –no-pause
1 | function main() { |
Non-ASCII有一些不可视, 所以可以先编码打印出来, 再用编码后的字符串去 hook.
1 | int ֏(int x) { |
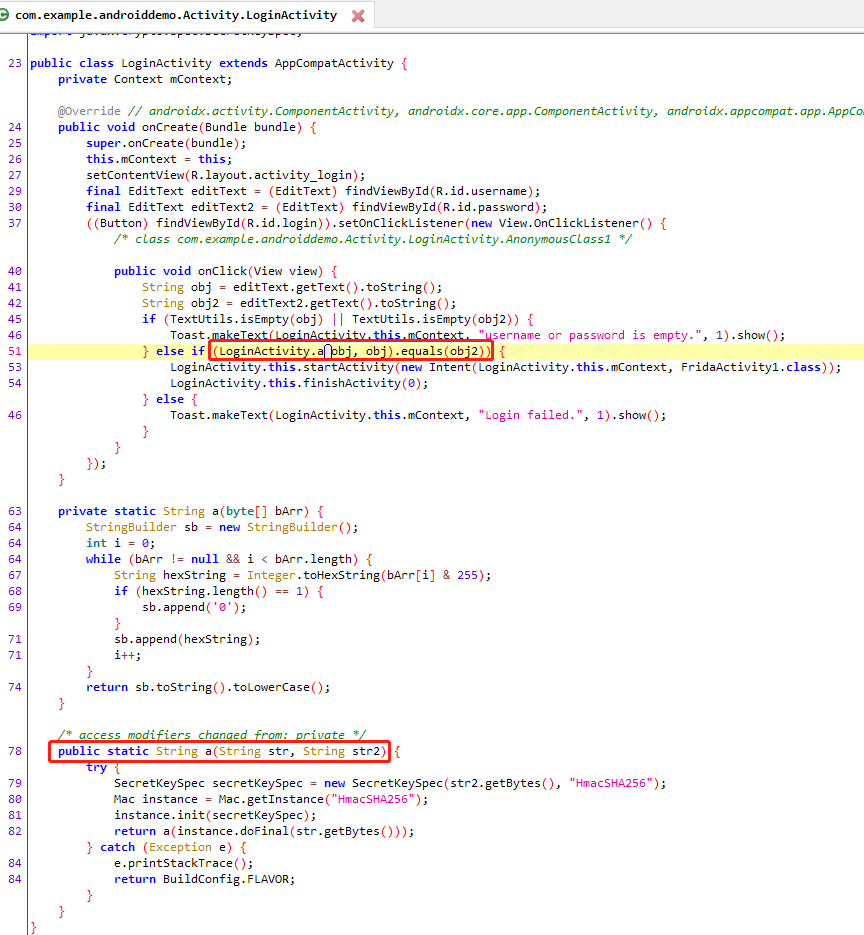
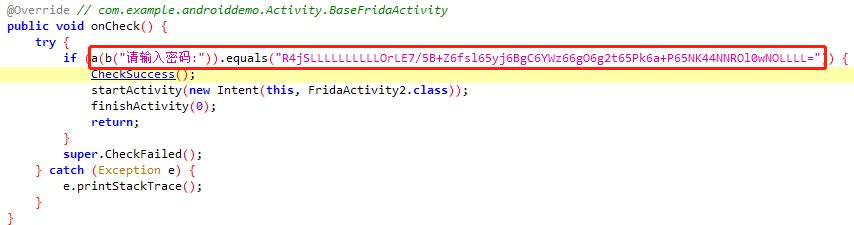
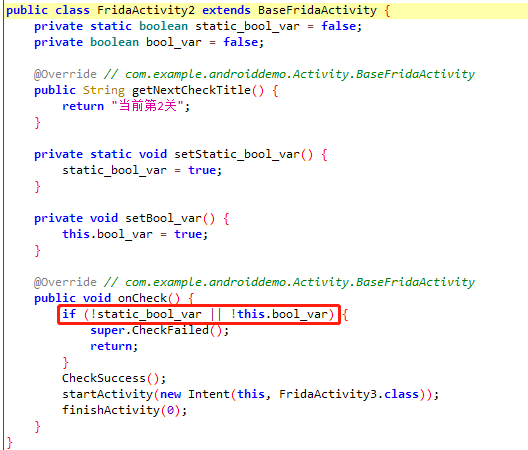
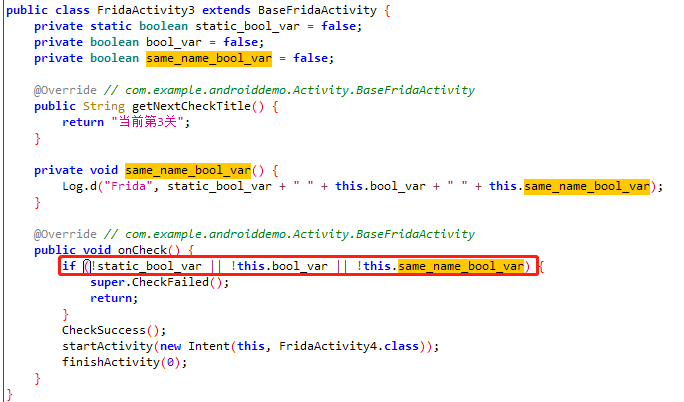
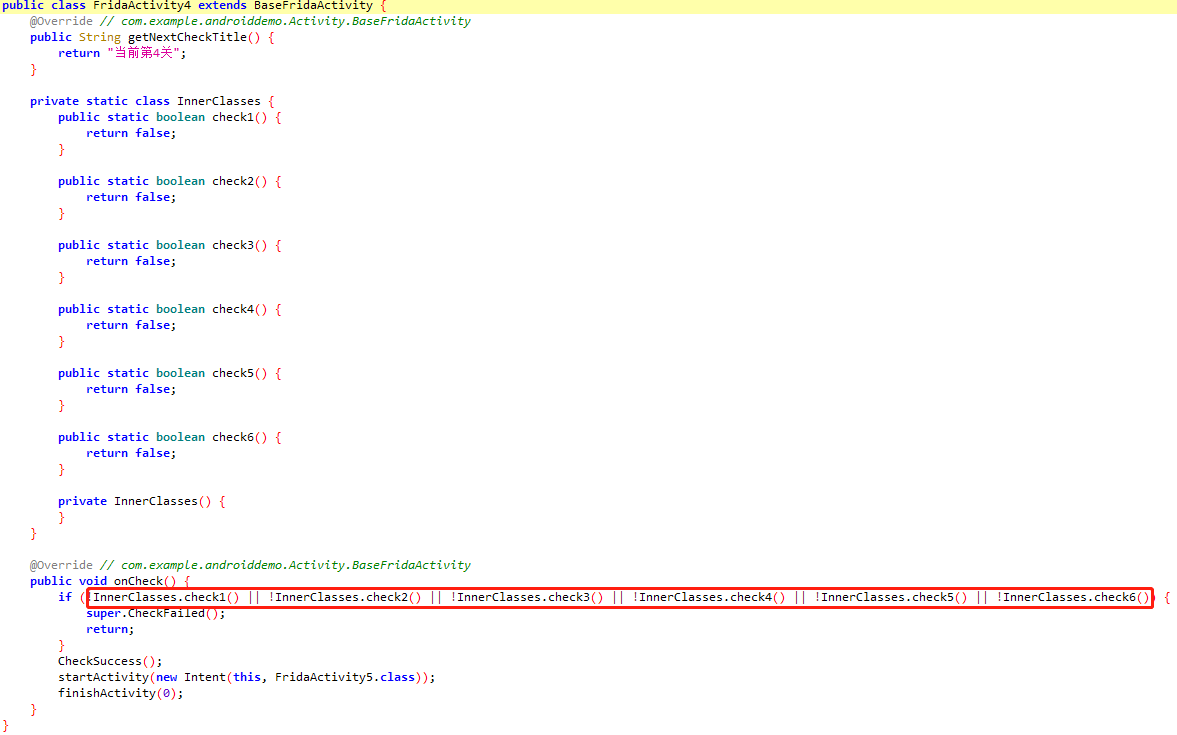
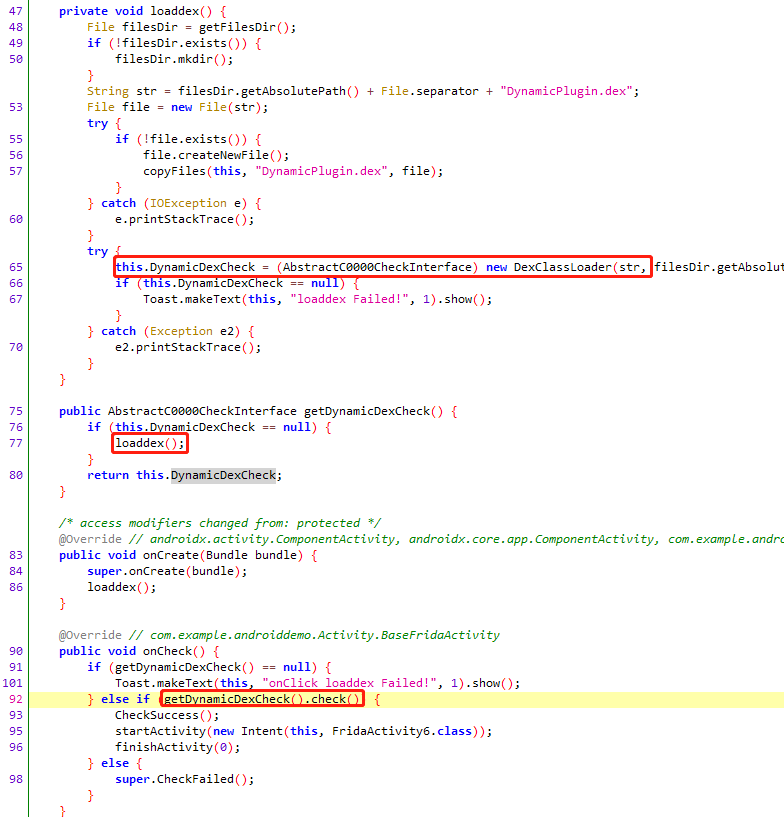
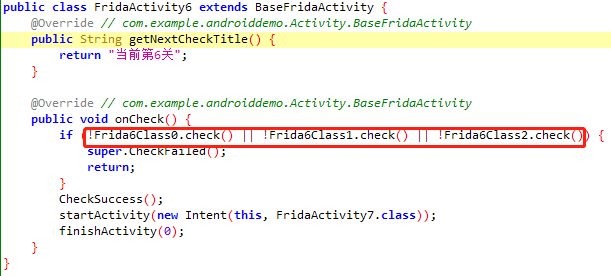
六层锁机案例
objection -g com.example.androiddemo explore
1 | function main(){ |
1 | function second(){ |
1 | function third(){ |
1 | function forth(){ |
1 | function fifth(){ |
1 | function sixth (){ |
获取枚举所有实现类
1 |
|
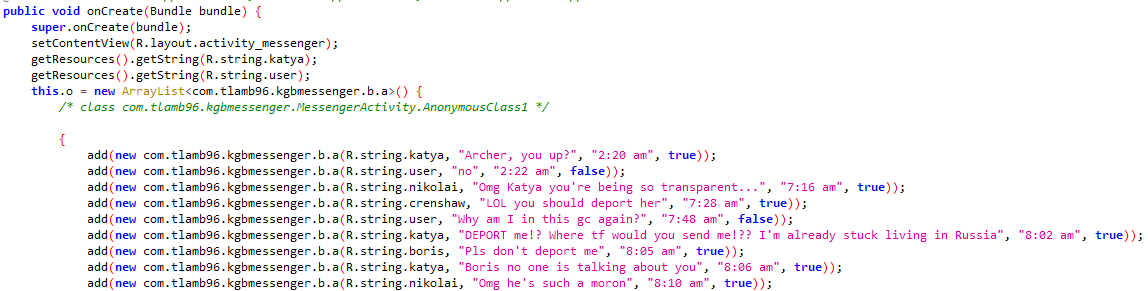
kgb-messenger
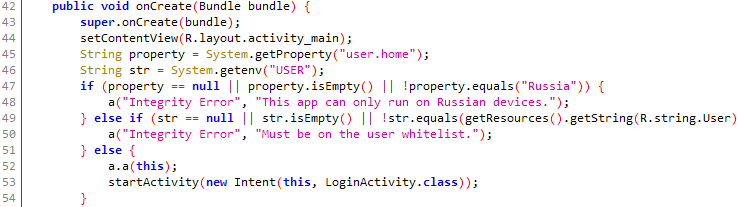
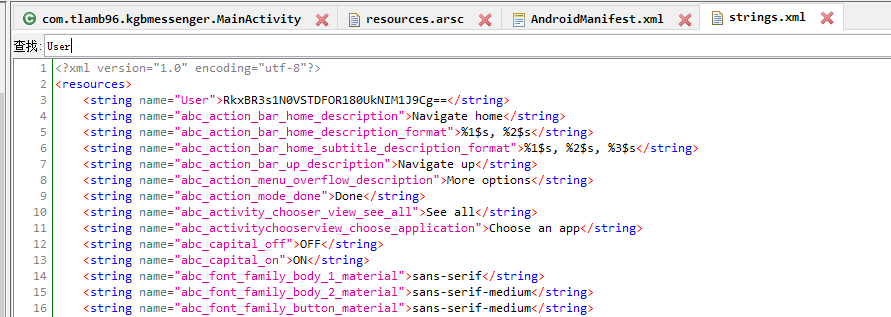
R.string.User在资源文件的resources.arsc/res/valus/strings.xml
1 | function hook_java() { |
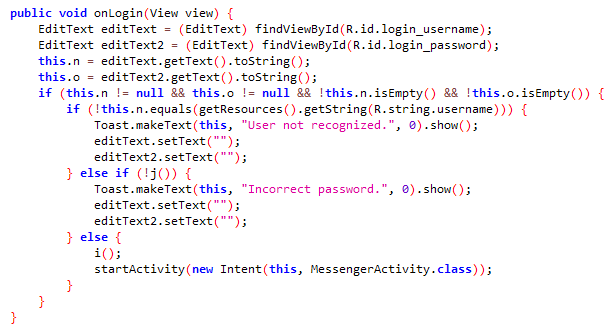
R.string.username在资源文件的resources.arsc/res/valus/strings.xml
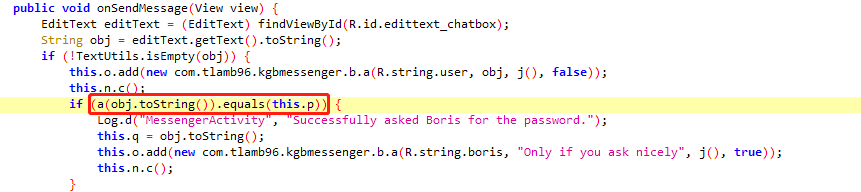
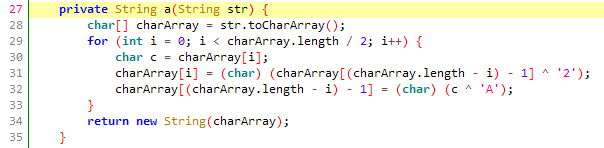
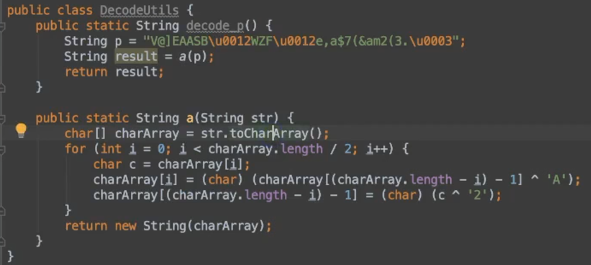
1 | function hook_java() { |
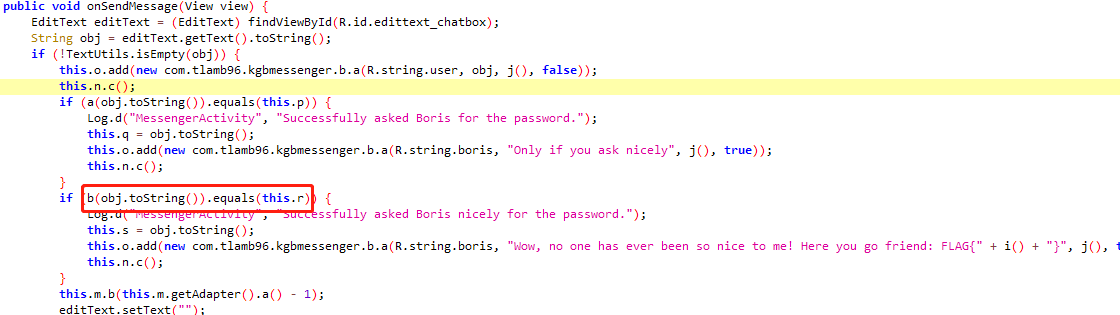
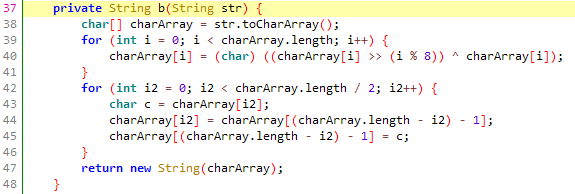
先解密r为text字符串,需要用到z3的库
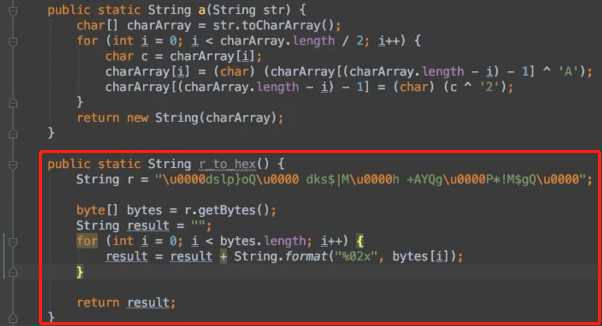
1 | jar -cvf ddex.jar com/example/androiddemo/DecodeUtils.class |
1 | from z3 import * |
xman
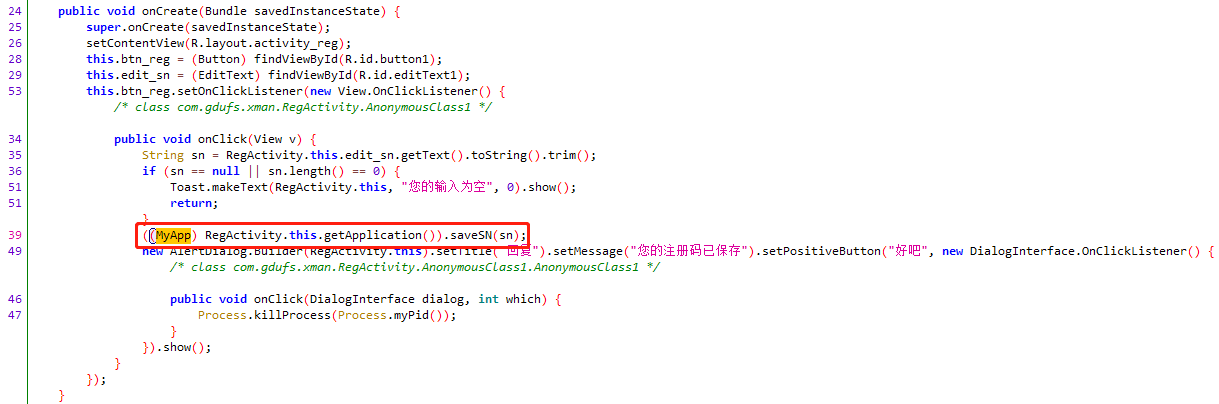
1 | function hook_java() { |
由于搜索导出函数没有saveSN,查看JNI_OnLoad和.init_array(ctrl+s没有函数),当registerNative不好找时**
frida_hook_libart**
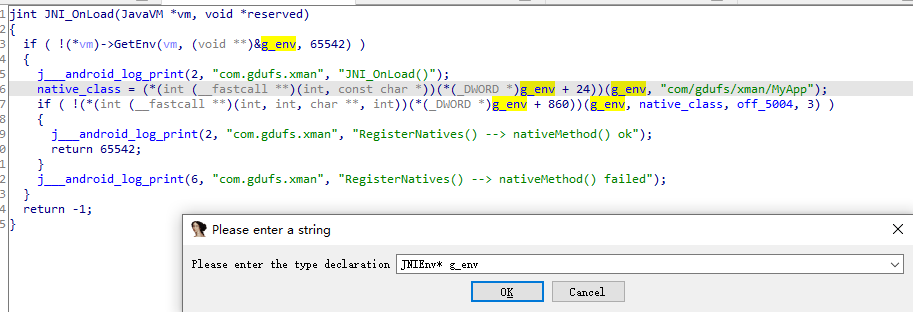
off_5004是函数数组,双击进入
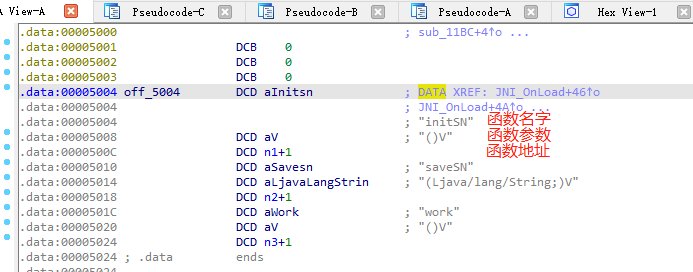
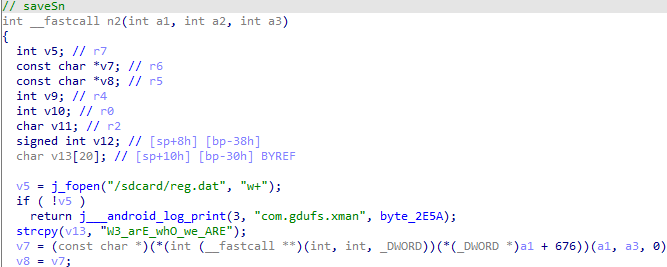
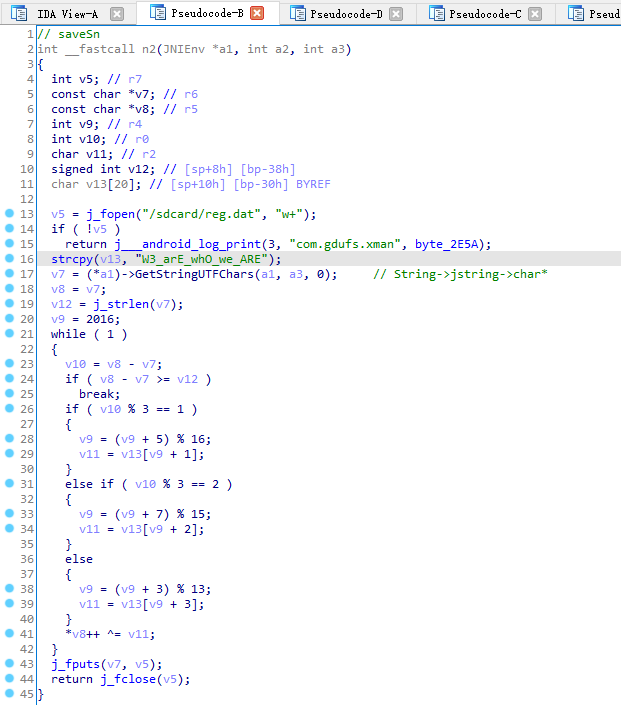
saveSN在n2中,双击进入
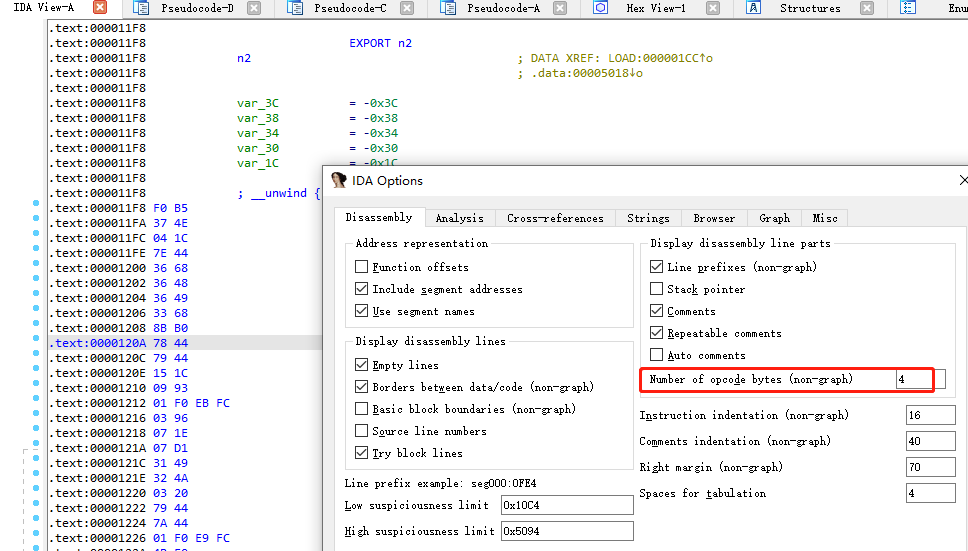
进入text View模式,设置opcode字节为4,函数开头2字节,中间4字节,是thumb格式函数,基地址+1才能正确hook
1 | function hook_native() { |
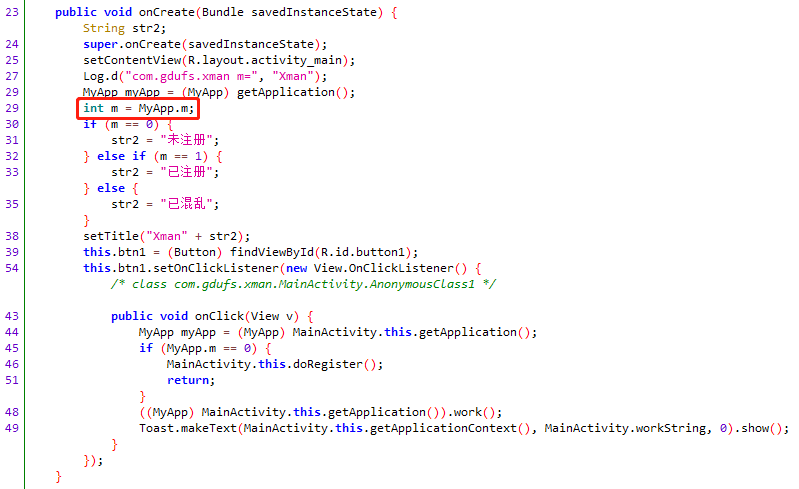
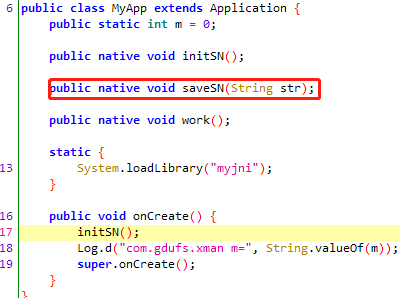
MyApp中m=0,需要找到哪里对m设值,在initSN中n1函数
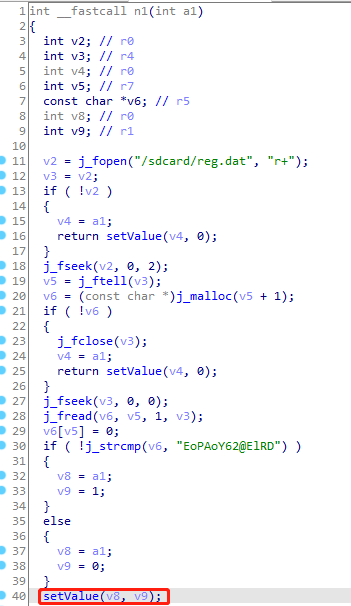
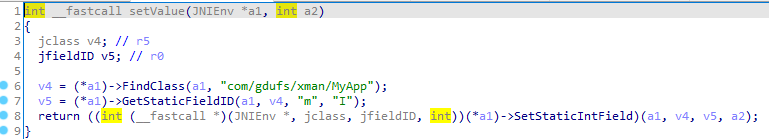
1 | function hook_libart() { |
需要在n1函数中strcmp返回true时将v9设置为1
1 | function hook_libc() { |
将/sdcard/reg.dat中内容改为EoPAoY62@ElRD即可
1 | function write_reg_dat() { |
RPC
主动调用
lesson7lesson4.js
1 | function invoke(){ |
lesson7loader.py
1 | import time |
接受回调
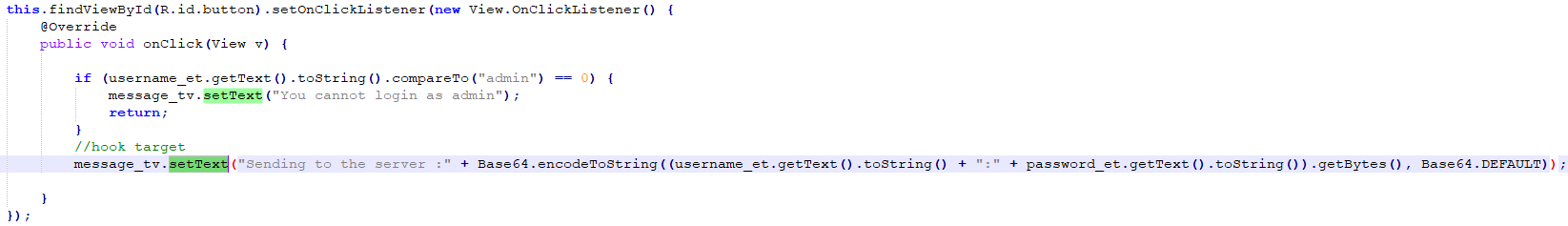
lesson7sec.js
1 | Java.perform(function(){ |
lesson7secloader.py
1 | import time |
NPS
内网穿透代理,linux_amd64_server.tar.gz服务端,linux_amd64_client.tar.gz客户端,
1 | sudo ./nps install |
新增客户端,复制客户端命令在客户端运行即可
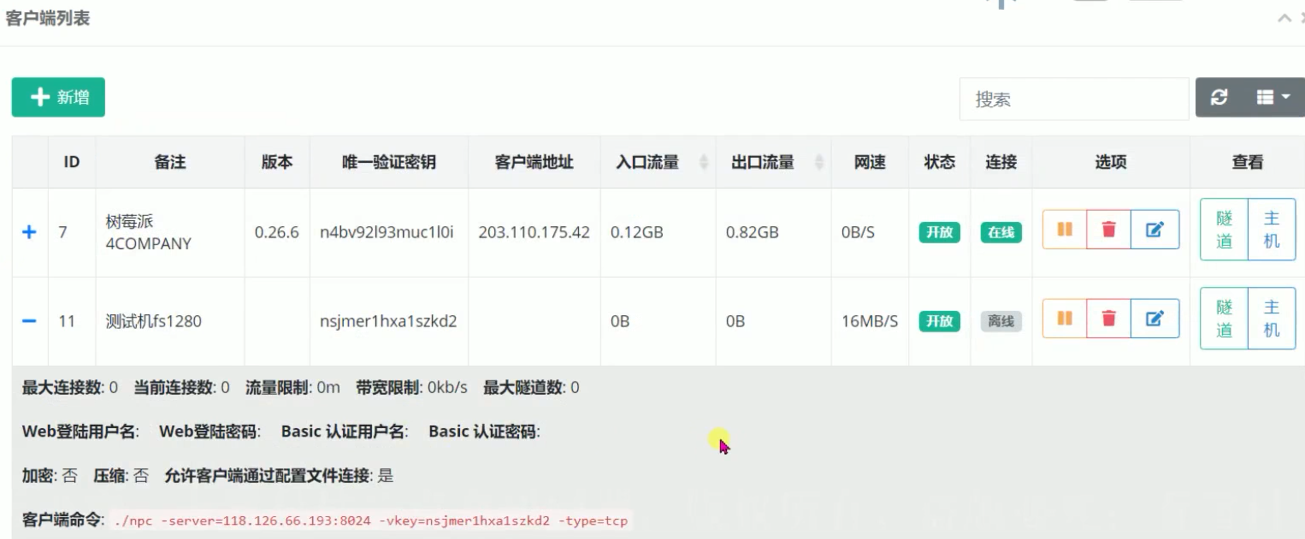
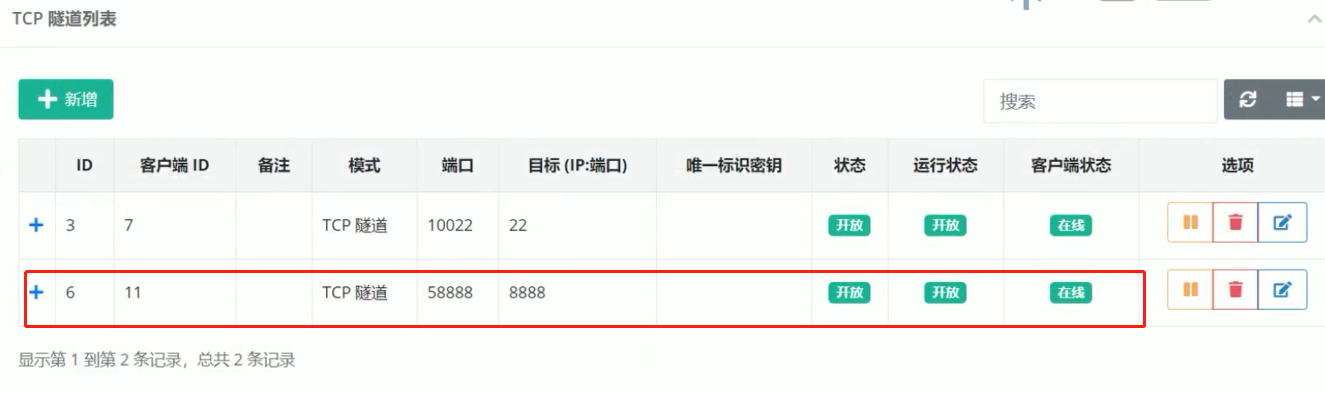
客户端启动frida ./fs1280arm64 -l 0.0.0.0:8888 ,新增TCP隧道,将内网端口8888映射到公网58888,其中的目标可以填入很多IP:端口进行映射
Zentrace
批量hook
1 | # pyenv install 3.8.0 |
- 点击打开“设置”应用;
- 选择
Action→Match RegEx - 输入
E:java.io.File,点击add,然后关闭窗口 - 点击
Action→Start
可以观察到java.io.File类的所有方法都被hook了,,并且像java.io.File.createTempFile方法的所有重载也被hook了
- 点击
Action→Stop,再点击Action→Clean,本次观察结束。 - 也可以使用模糊匹配模式,比如输入
M:java.io.File之后,会将诸如java.io.FileOutputStream类的诸多方法也都hook上,不过无法打印调用栈,无法hook构造函数,也就是$init。
案例
过弹窗
1 | android hooking list activities |
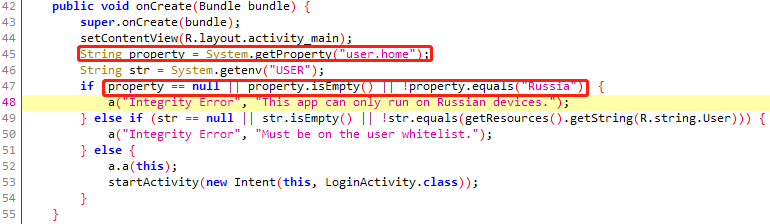
1 | function main(){ |
过登录
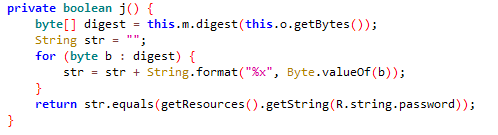
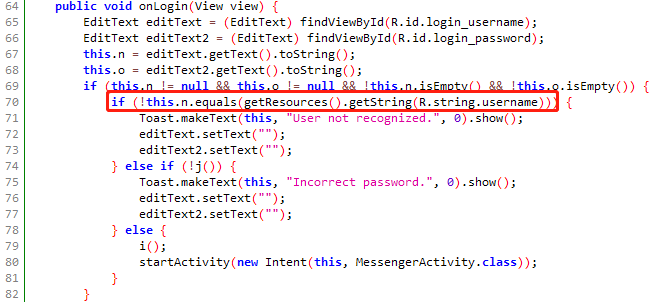
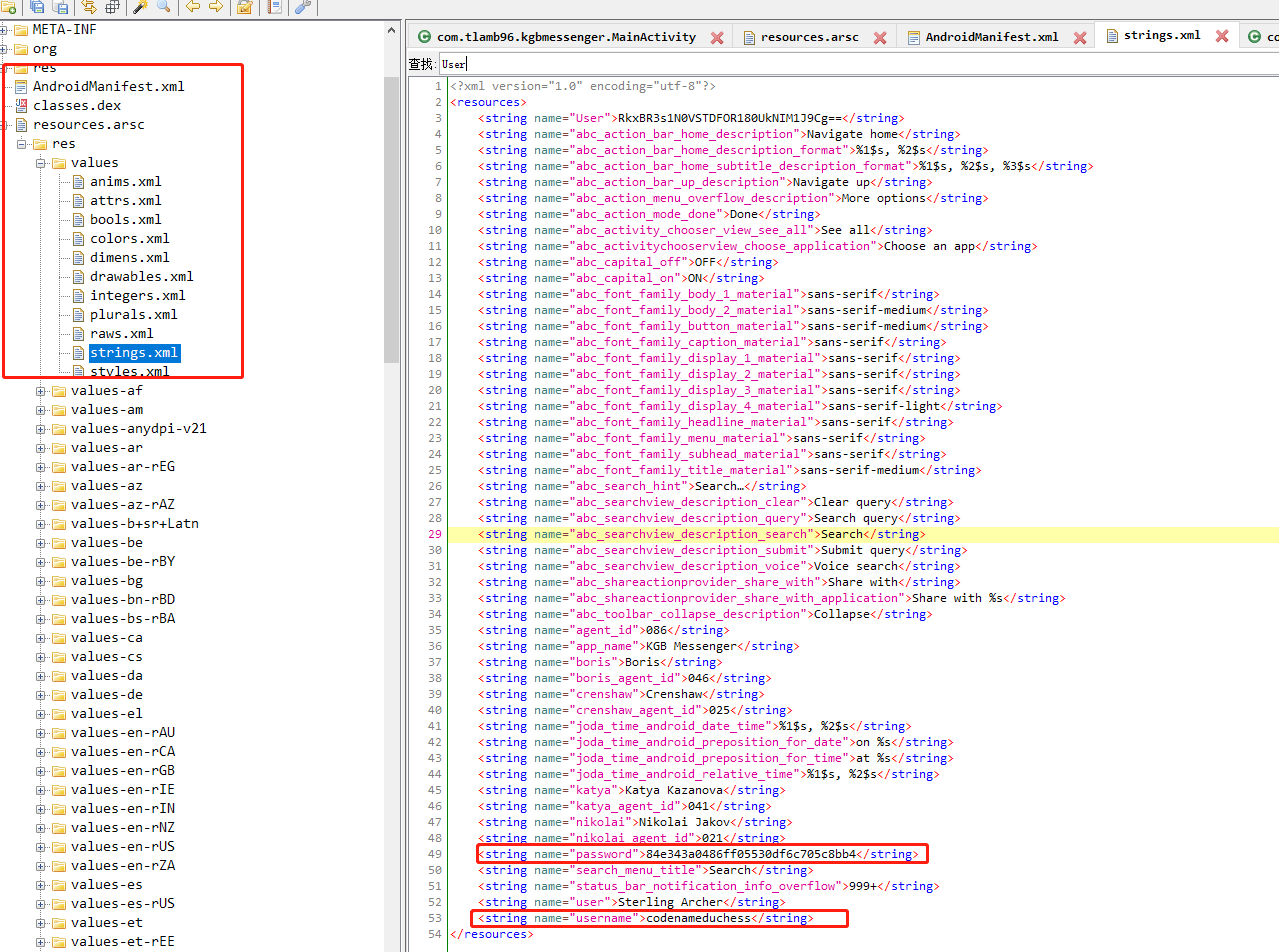
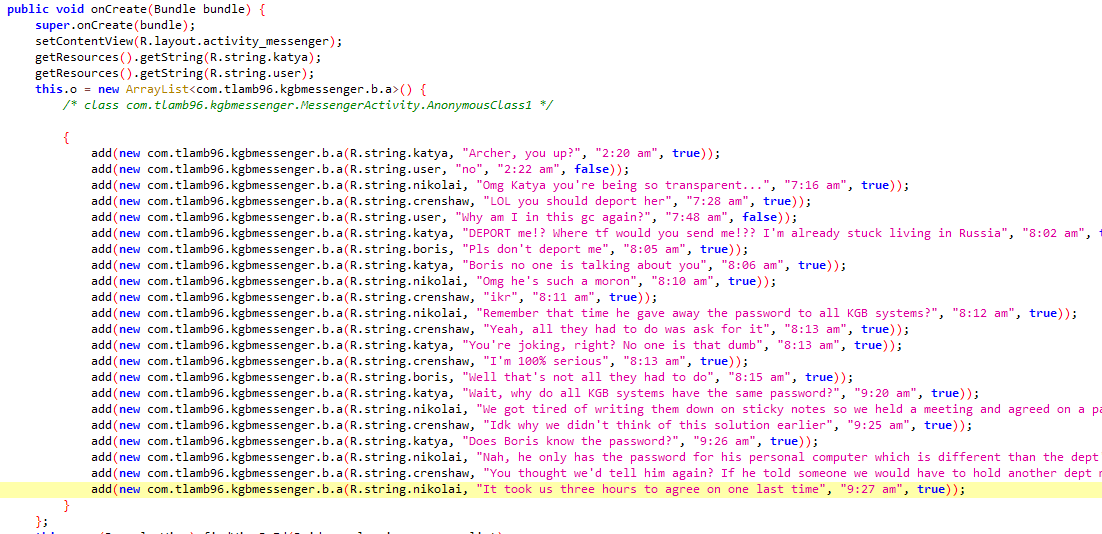
username:codenameduchess
password:guest
1 | function main(){ |
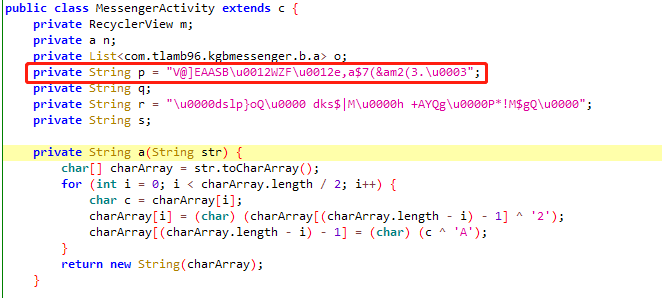
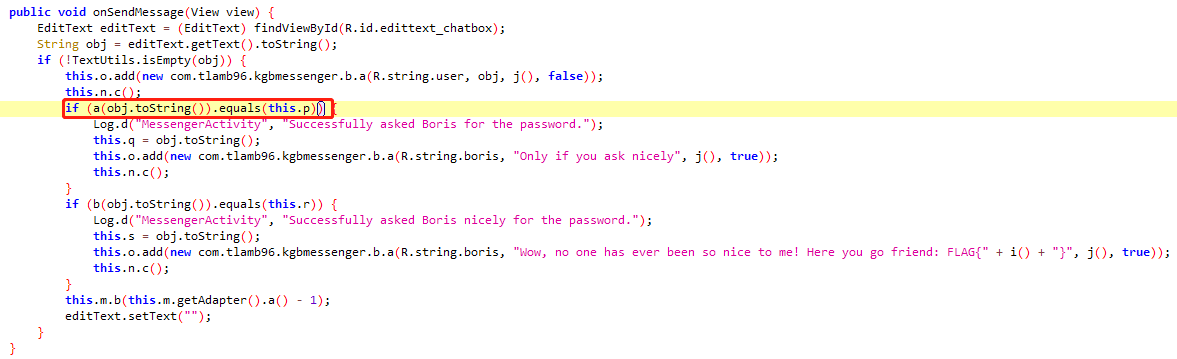
1 | function main(){ |
逆向实现
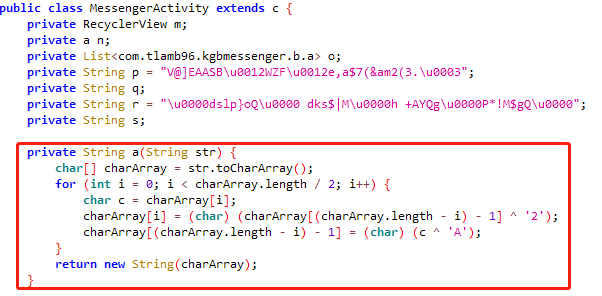
1 | public class reverseA { |
将class文件打包成dex,d8 reverseA.class
1 | function main(){ |
pip install z3-solver
1 | from z3 import * |
adb shell
input text “aaa” 输入adb

