抓包
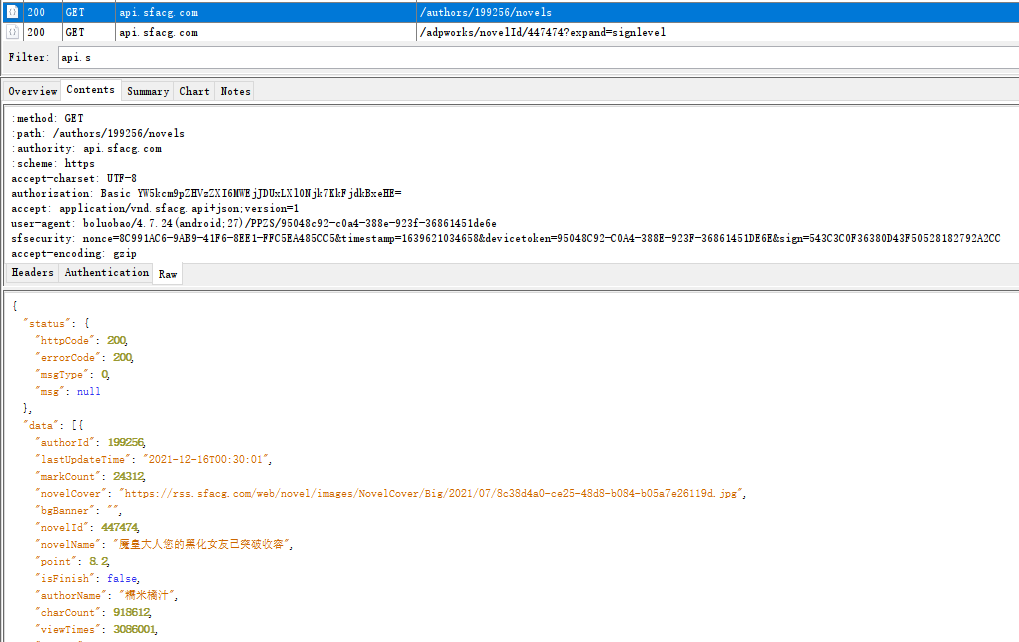
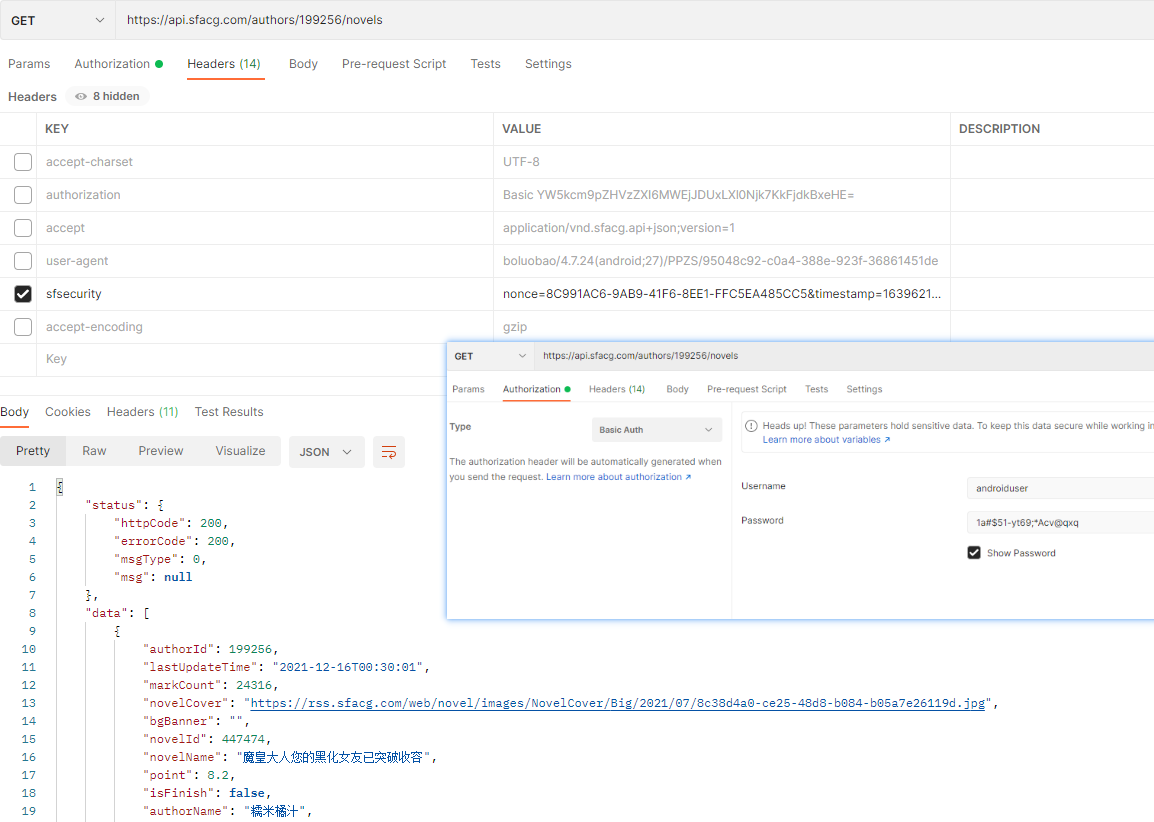
postman发起请求
脱壳
1 | proxychains git clone https://github.com/hluwa/FRIDA-DEXDump.git 移到~/.objection/plugins重命名为dexdump |
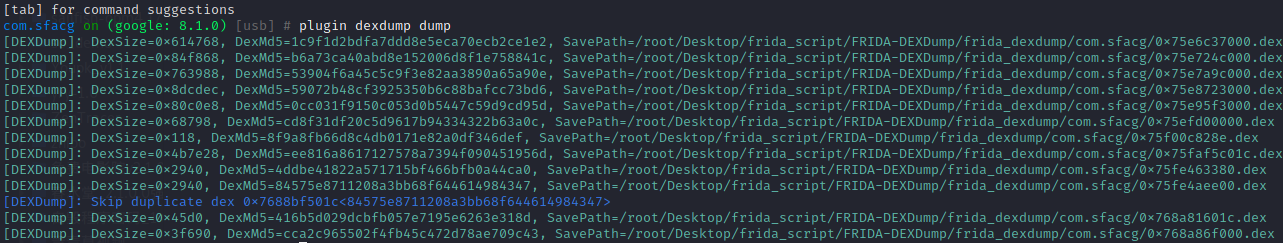
上图可见,脱壳效果并不好。不过不影响,搜索sfsecurity
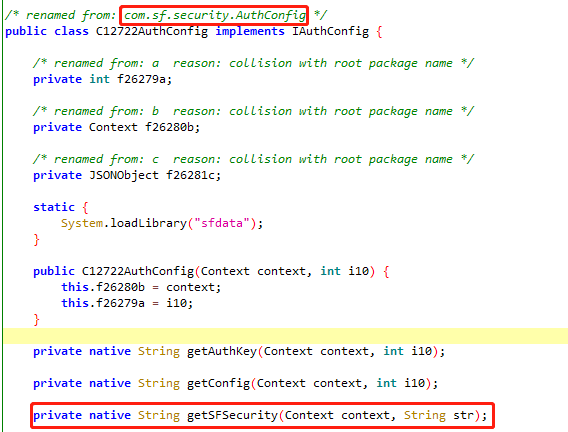
1 | plugin wallbreaker objectsearch com.sf.security.AuthConfig |
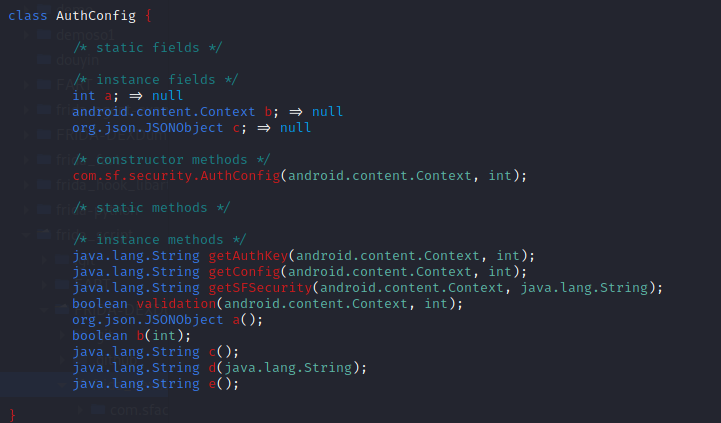
1 | android hooking watch class_method com.sf.security.AuthConfig.getSFSecurity --dump-args --dump-backtrace --dump-return |
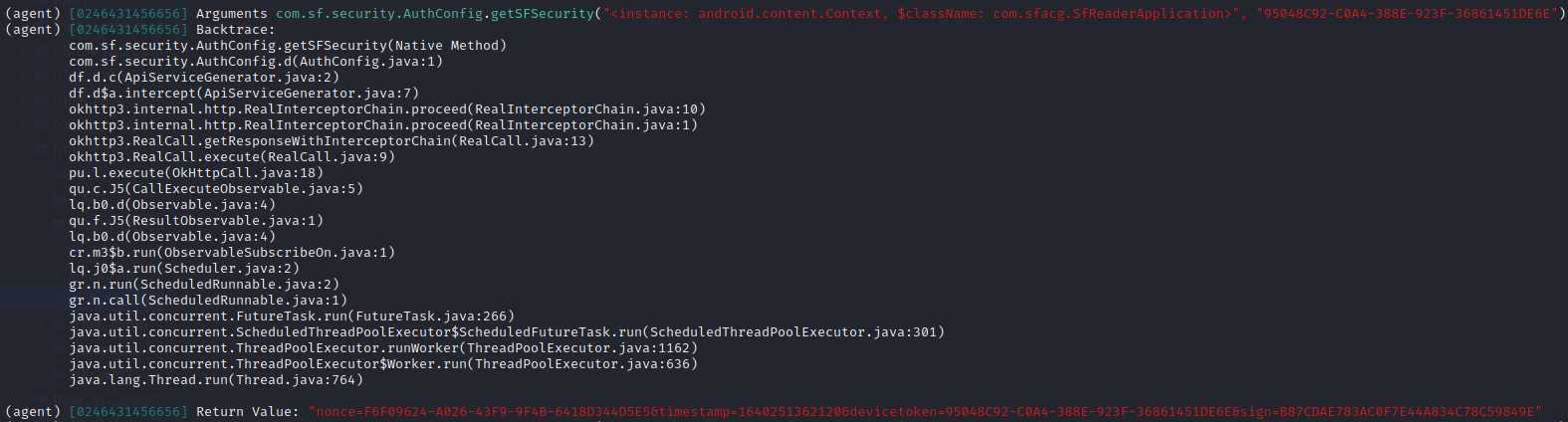
入参为context和token,根据输出的结果,包含了nonce和sign两个加密键值对,timestamp时间戳,devicetoken是第二个参数。
Unidbg
通过IDA的导出函数找到getSFSecurity的起始地址,尝试主动调用
1 | public class qxs extends AbstractJni{ |
运行在调用callStaticObjectMethodV时报错:java.lang.UnsupportedOperationException: java/util/UUID->randomUUID()Ljava/util/UUID;,补环境
1 | @Override |
运行在调用callObjectMethodV时报错:java.lang.UnsupportedOperationException: java/util/UUID->toString()Ljava/lang/String;,补环境
1 | @Override |
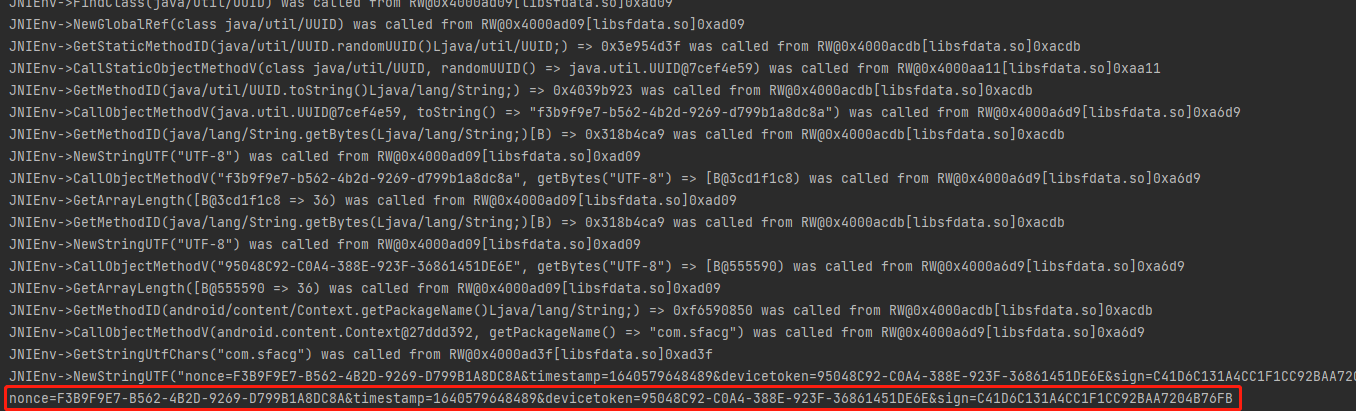
正常获取到结果,可以证明nonce就是通过uuid生成的随机数,timestamp就是当前时间戳,deviceToken就是传入的参数,sign就是生成的结果。
Sign
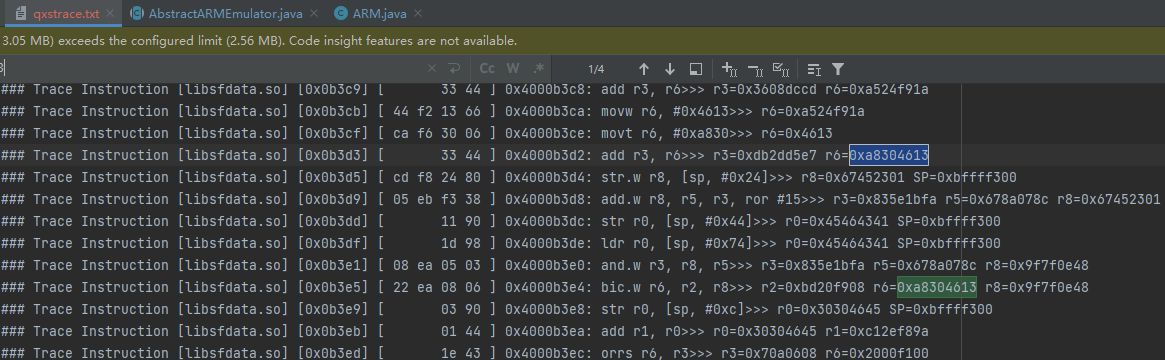
本so进行了保护,无法反编译,findHash也没有结果,但是unidbg可以正常跑出加密后的sign,尝试使用traceCode追踪下汇编指令流。
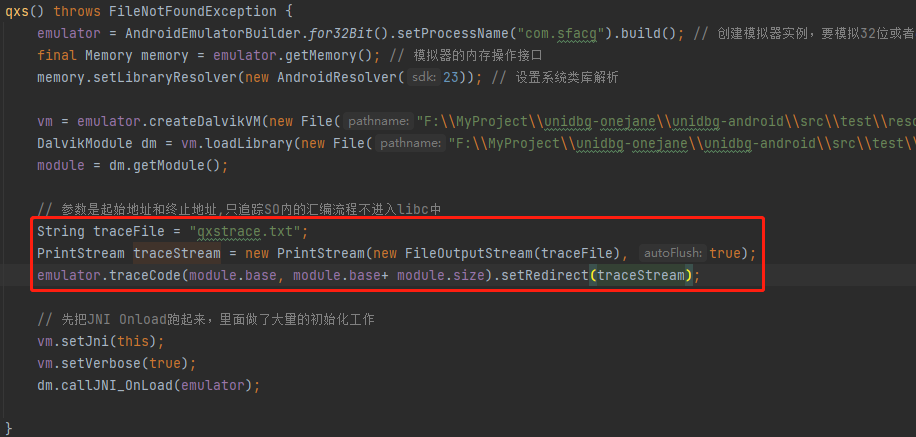
默认的unidbg的trace是不保存寄存器值的信息的,修改ARM32下的AbstractARMEmulator.java
1 | private void printAssemble(PrintStream out, Capstone.CsInsn[] insns, long address, boolean thumb) { |
在ARM.java中新建SaveRegs方法
1 | public static String SaveRegs(Emulator<?> emulator, Set<Integer> regs) { |
开始跑traceCode并将结果保存在qxstrace.txt中,由于sign是32位的十六进制数,猜测是md5相关,关键特征有4个魔数和64个K。
1 | # 魔数 |
通过检索这些关键特征,可以断定这是一个md5或者魔改后的md5