篇幅有限
完整内容及源码关注公众号:ReverseCode,发送 冲
https://www.lagou.com/
抓包
登录url:
GET https://passport.lagou.com/login/login.json
参数:
1
2
3
4
5
6
7
| jsoncallback: jQuery11130510950445912626_1618227551741
isValidate: true
username: 15806204095
password: 990eb670f81e82f546cfaaae1587279a
request_form_verifyCode:
challenge: c7a96a290ed4d75ca2a8bf139172dbe0
_: 1618227551745
|
分析
参数中password和challenge看起来是加密参数,其实challenge是极验验证码请求的参数,本文针对password进行参数分析,暂时先不做讨论。
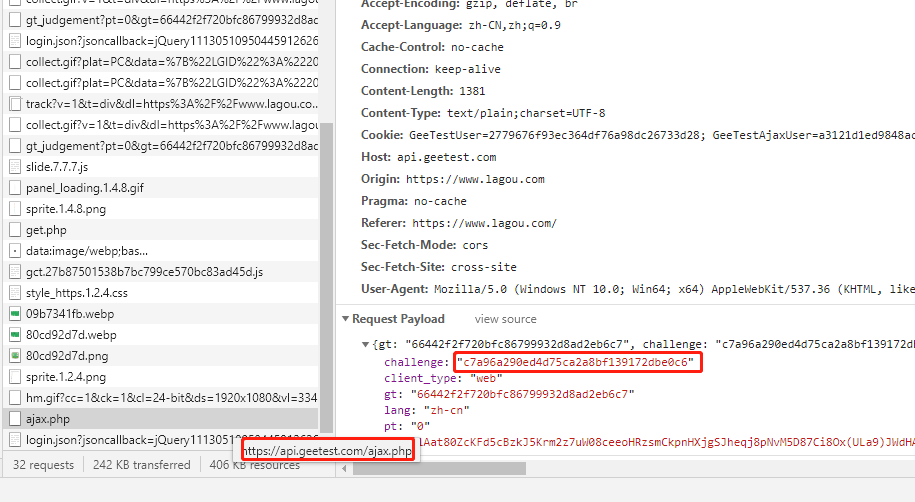
搜索login/login.json并格式化js后,发现改password通过md5实现加密,在Watch界面输入g查看g的内容
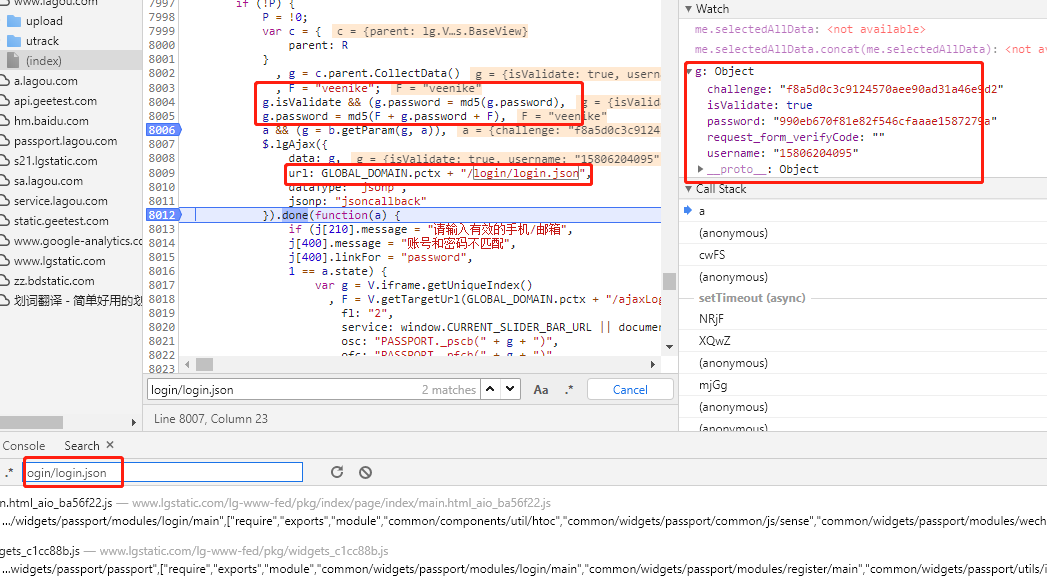
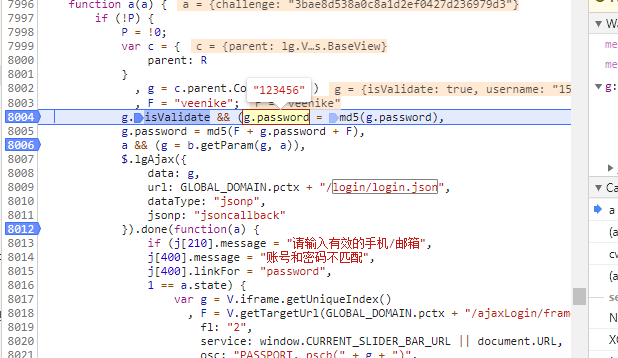
放行程序后,在g.isValidate && (g.password = md5(g.password)处重新打上断点并登录
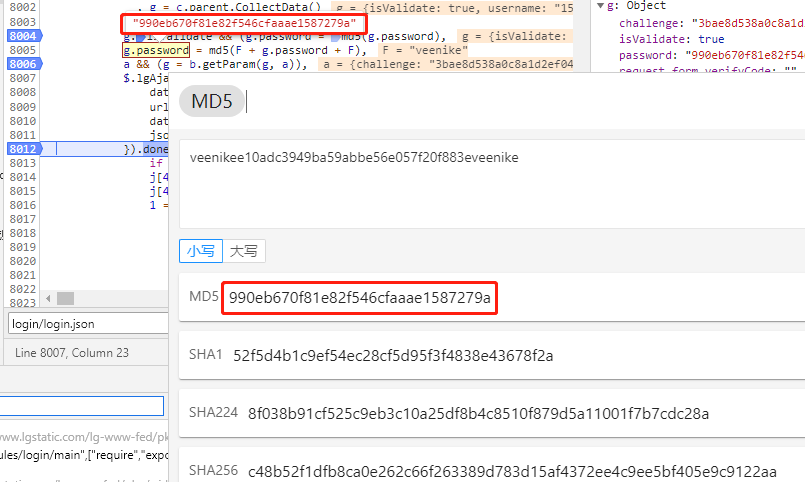
那么分析得出password=md5(“veenike”+md5(passwrod)+”veenike”)
爬虫实现
1
2
3
4
5
6
7
8
9
10
| import requests
from hashlib import md5
username = '15806204095'
pwd = '123'
md5_pwd = md5(("veenike" + md5(pwd.encode('utf8')).hexdigest() + "veenike").encode("utf8")).hexdigest()
print(md5_pwd)
url = 'https://passport.lagou.com/login/login.json?jsoncallback=jQuery111306946515748870927_1618229101639&isValidate=true&username='+username+'&password=+'+md5_pwd+'+&request_form_verifyCode=&challenge=c3bebcad0648898aa58cb3f4dbf2f820&_=1618229101642'
r =requests.get(url)
print(r.text)
|
完整源码请关注微信公众号:ReverseCode,回复:JS逆向





