篇幅有限
完整内容及源码关注公众号:ReverseCode,发送 冲
需求
最近在电商业务的设计中要求像识货app一样实现选好型号尺寸之类的商品属性后,跳转到淘宝时携带这些参数帮助用户自行选中,如下图所示:
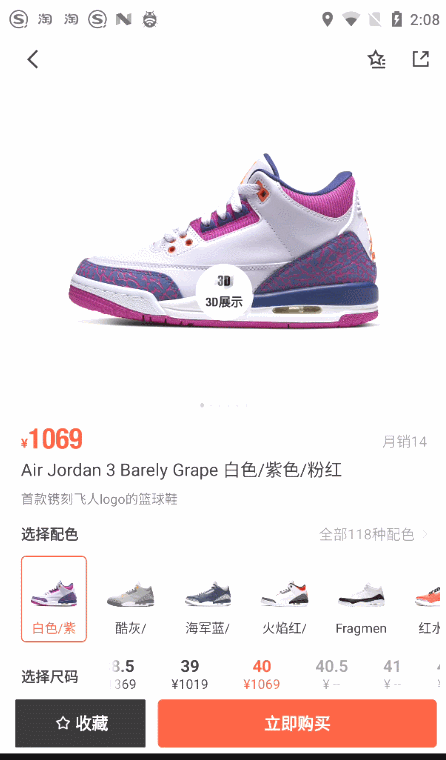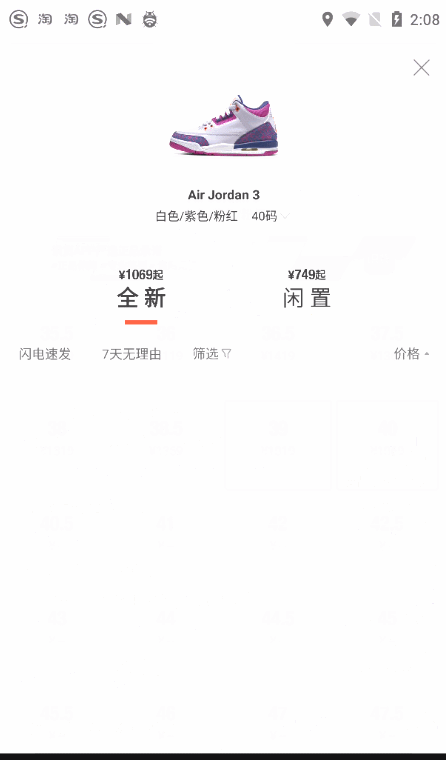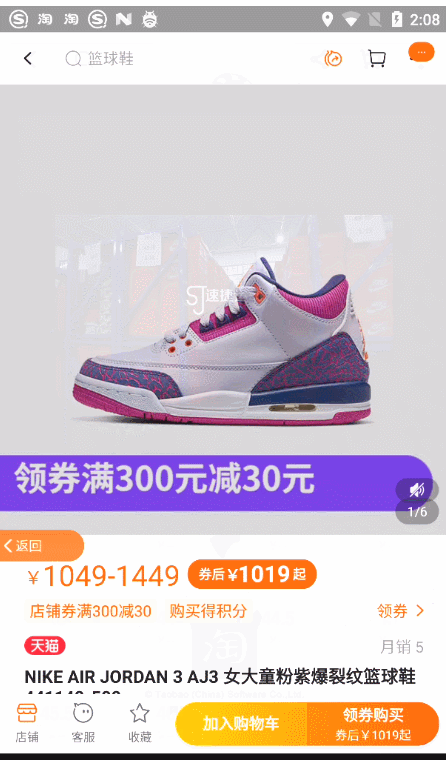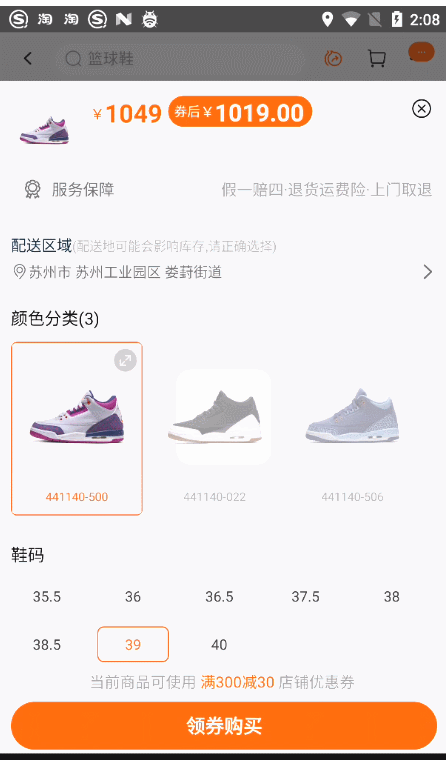
分析
- 启动frida-server;
1 | adb shell |
- 使用PKiD判断是否加壳;
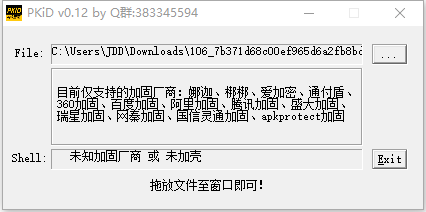
- 安装好识货app,由于没有加固,直接从AndroidMainfest.xml中拿到包名。jadx-gui *.apk 查看,
package="com.hupu.shihuo"找到包名; - hook点击事件获取触发的类
frida -UF -l hookEvent.js
1 | pyenv local 3.8.2 该环境的frida版本为12.8.0 |
- 点击尺寸型号时,选择配色尺码触发事件
1 | [Google Pixel XL::识货]-> [WatchEvent] onClick: cn.shihuo.modulelib.views.widget.easyrecyclerview.adapter.RecyclerArrayAdapter$3 |
- 选好型号后,点击立即购买触发事件
1 | [Google Pixel XL::识货]-> [WatchEvent] onClick: com.module.shoes.view.DetailOfShoesBFragment$ab |
- 点击担保购买,查看触发事件
1 | [Google Pixel XL::识货]-> [WatchEvent] onClick: com.module.shoes.view.adapter.ChannelOfShoesAdapter$ViewHolder$a |
内存漫游
属性点击
1 | android hooking watch class cn.shihuo.modulelib.views.widget.easyrecyclerview.adapter.RecyclerArrayAdapter$3 --dump-args --dump-backtrace --dump-return 对整个RecyclerArrayAdapter类进行hook第三个匿名内部类 |
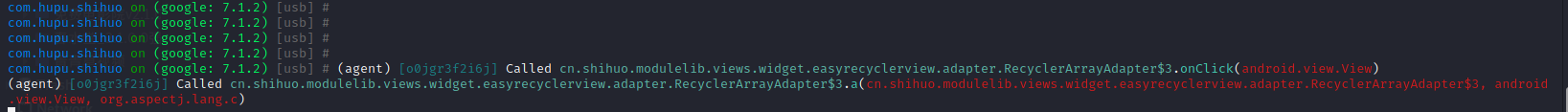
1 | jobs list |
1 | plugin wallbreaker objectsearch cn.shihuo.modulelib.views.widget.easyrecyclerview.adapter.RecyclerArrayAdapter$3 内存中搜索该匿名内部类 |
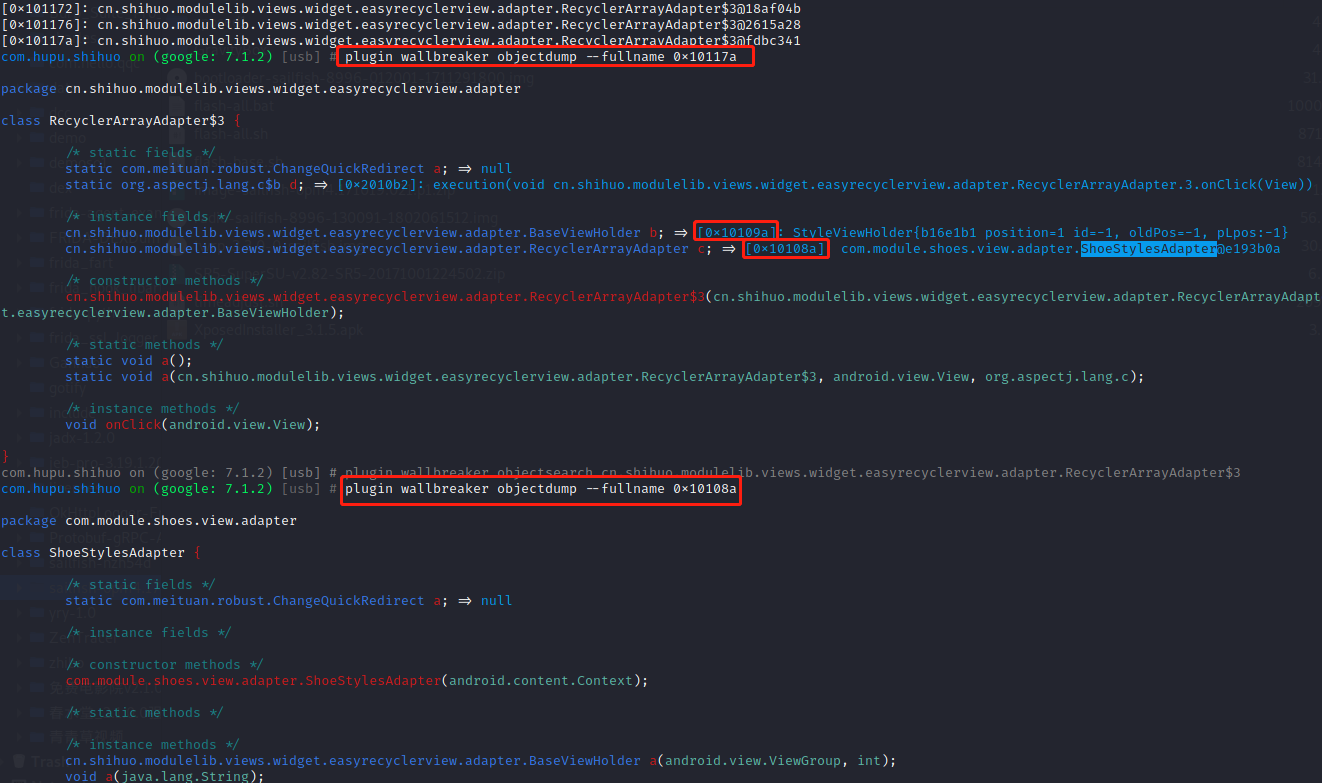
以上的类中没有任何线索涉及到参数的传递或者请求的跳转。
立即购买
1 | android hooking search classes DetailOfShoesBFragment$ab 内存中搜索DetailOfShoesBFragment内部类ab及涉及的方法 |
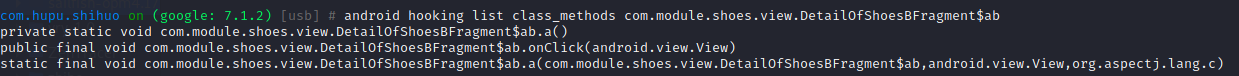
1 | android heap search instances com.module.shoes.view.DetailOfShoesBFragment$ab 获取内存实例 |
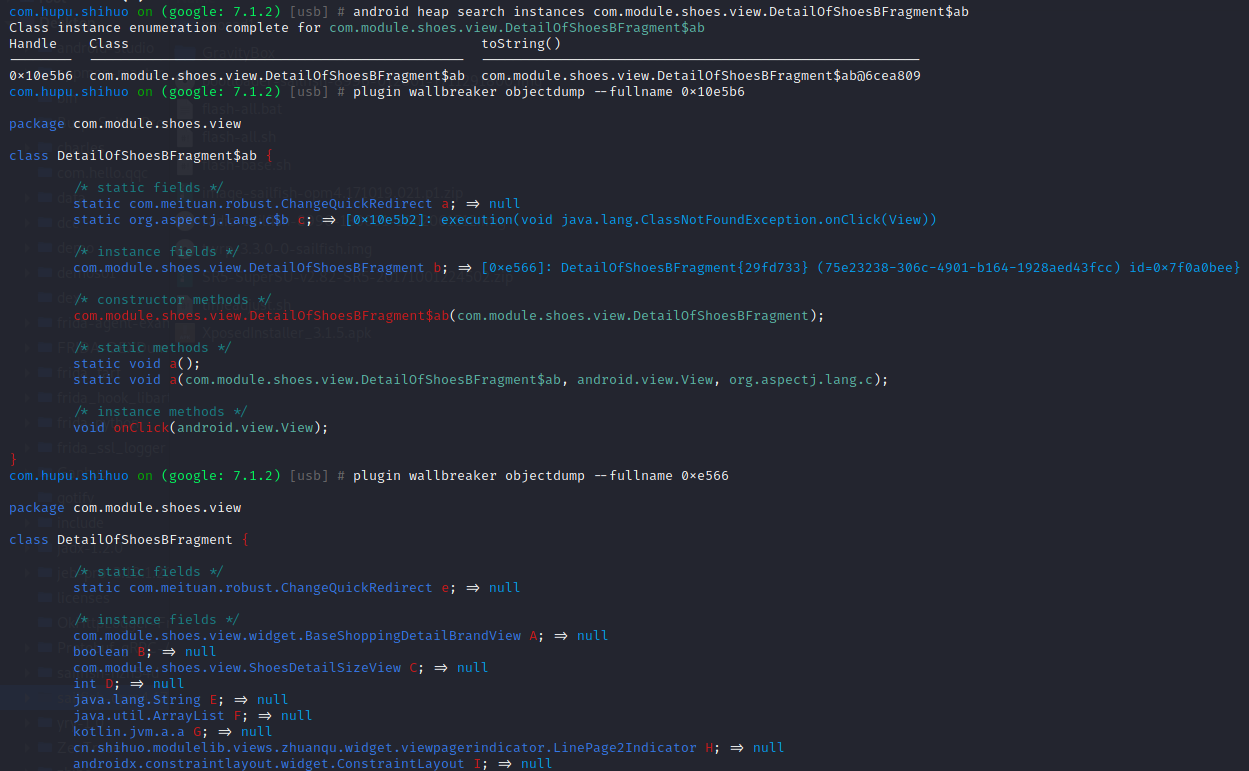
在DetailOfShoesBFragment实例中,ShoeDetailSecondModel极有可能有关键性线索实现参数携带跳转。
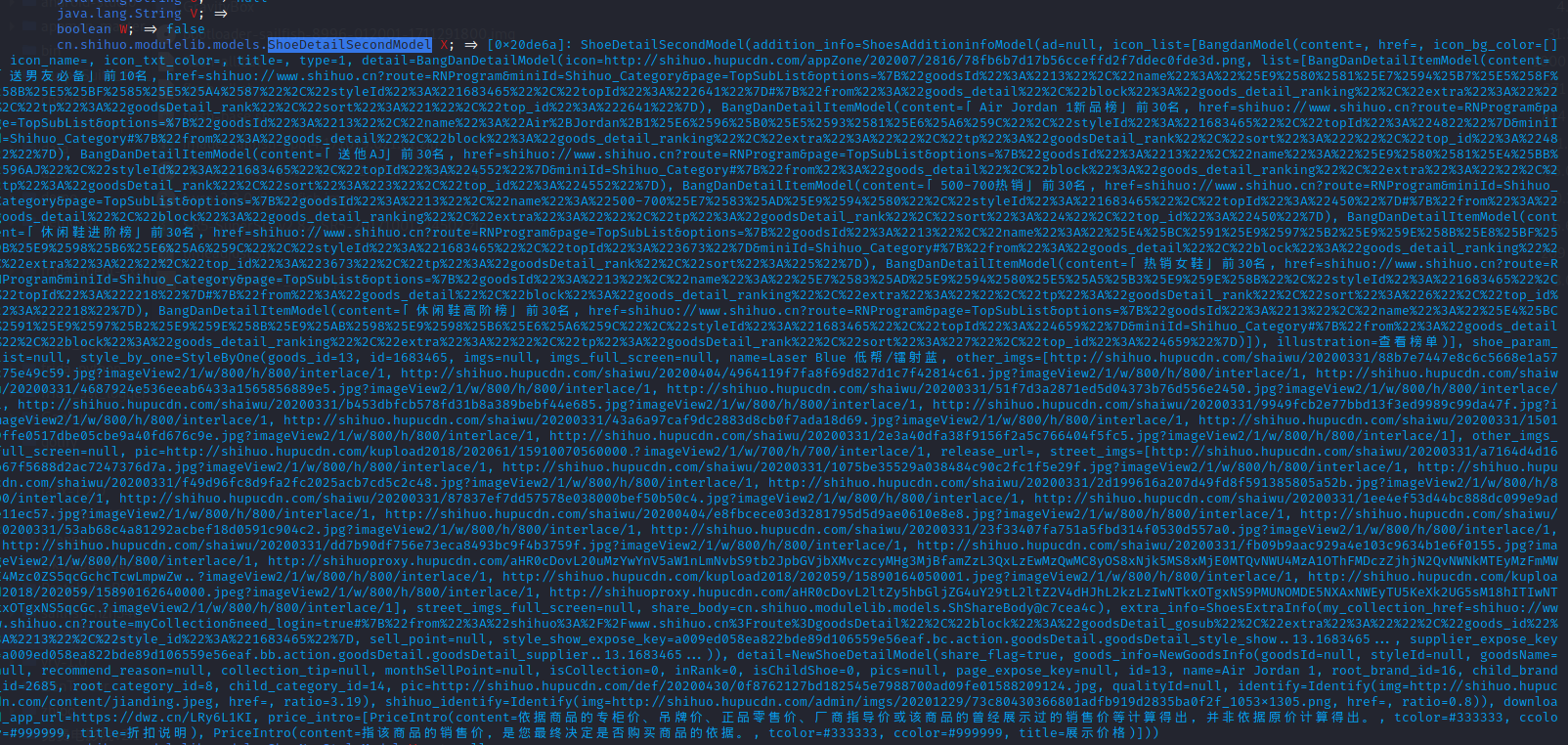
可是当我整个字符串拷贝下来时,发现连个taobao的毛都没看到,再次dump该实例,也没有什么重要线索。
担保购买
1 | android heap search instances com.module.shoes.view.adapter.ChannelOfShoesAdapter$ViewHolder$a 直接内存搜刮 |
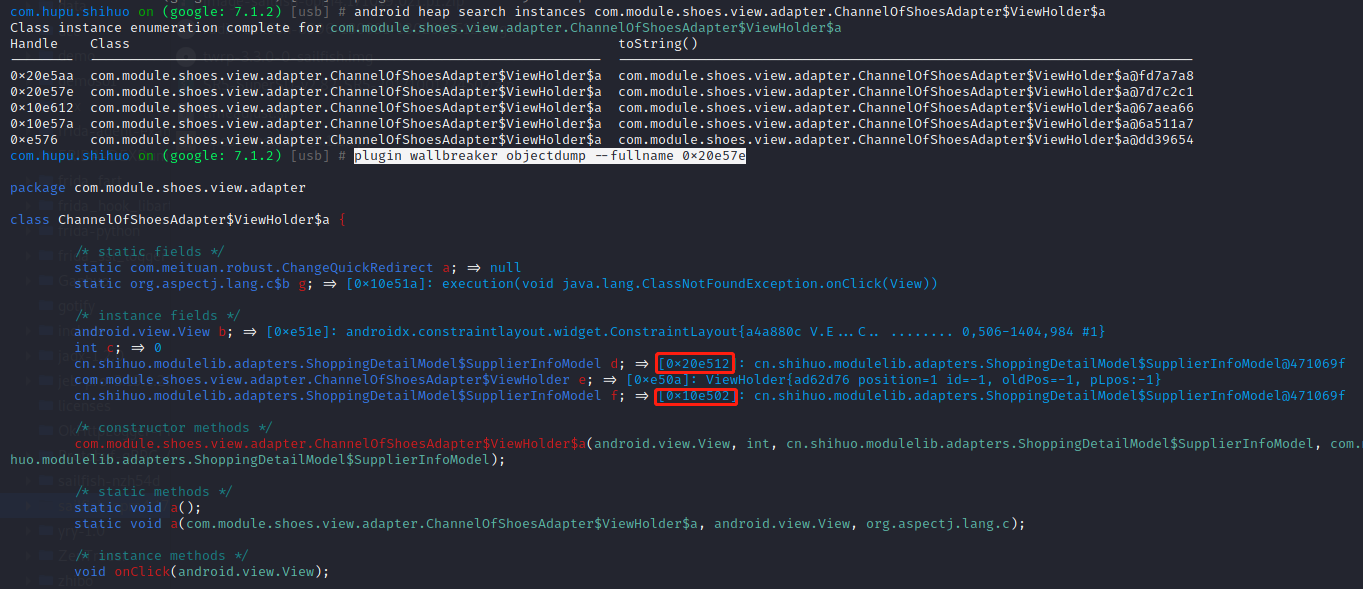
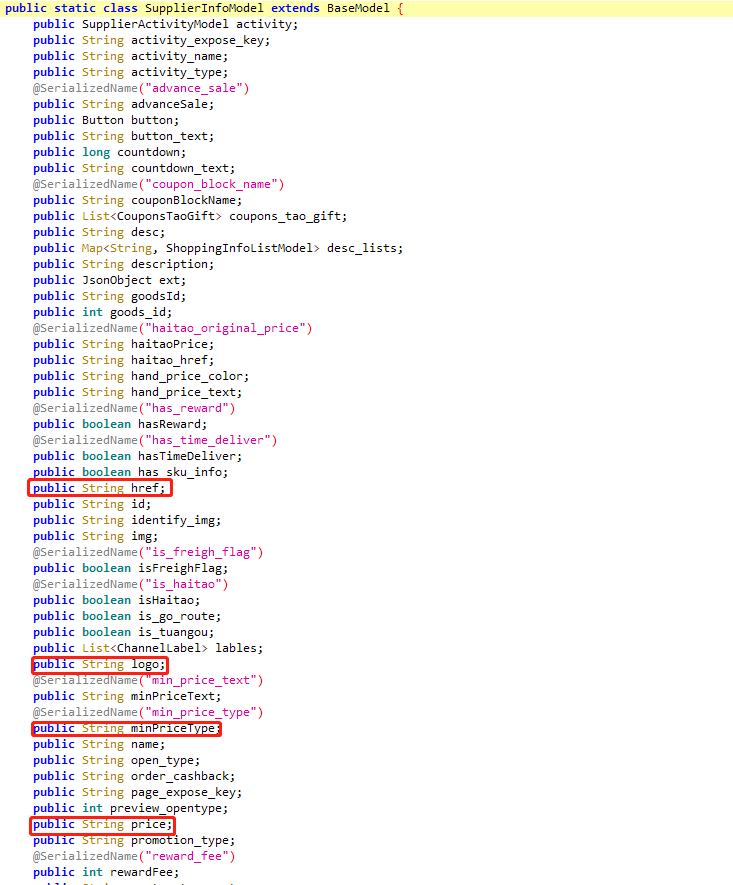
找到SupplierInfoModel类在jadx看源码是有一些关键性字段的,如price,href等。
1 | plugin wallbreaker objectdump --fullname 0x20e512 |
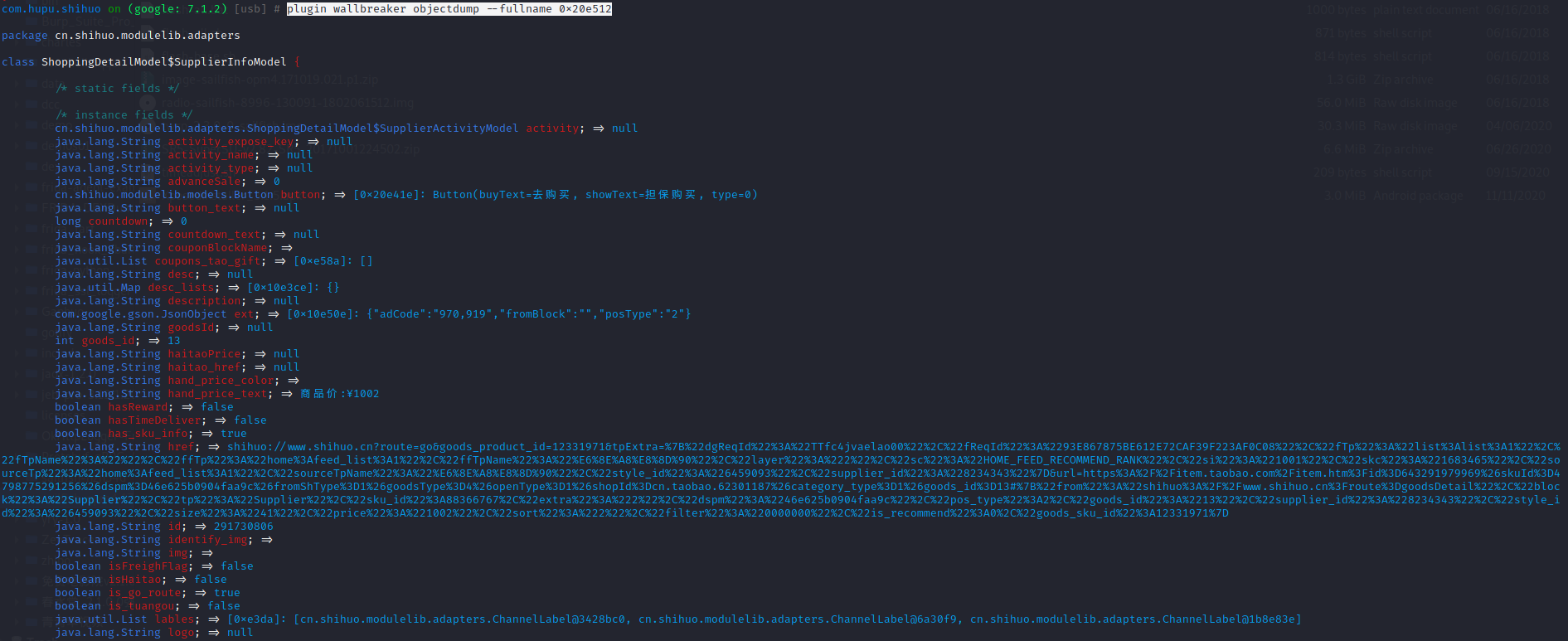
将这段href拷贝下来,解码后如下:
1 | shihuo://www.shihuo.cn?route=go&goods_product_id=12331971&tpExtra={"dgReqId":"TTfc4jvaelao00","fReqId":"93E867875BE612E72CAF39F223AF0C08","fTp":"list:list:1","fTpName":"","ffTp":"home:feed_list:1","ffTpName":"推荐","layer":"2","sc":"HOME_FEED_RECOMMEND_RANK","si":"1001","skc":"1683465","sourceTp":"home:feed_list:1","sourceTpName":"推荐","style_id":"6459093","supplier_id":"8234343"}&url=https://item.taobao.com/item.htm?id=643291979969&skuId=4798775291256&dspm=46e625b0904faa9c&fromShType=1&goodsType=4&openType=1&shopId=cn.taobao.62301187&category_type=1&goods_id=13#{"from":"shihuo://www.shihuo.cn?route=goodsDetail","block":"Supplier","tp":"Supplier","sku_id":88366767,"extra":"2","dspm":"46e625b0904faa9c","pos_type":2,"goods_id":"13","supplier_id":"8234343","style_id":"6459093","size":"41","price":"1002","sort":"2","filter":"0000000","is_recommend":0,"goods_sku_id":12331971} |
很明显这段是识货自行封装的协议,后面参数url=应该就是跳转到淘宝的链接。
将https://item.taobao.com/item.htm?id=643291979969&skuId=4798775291256&dspm=46e625b0904faa9c&fromShType=1&goodsType=4&openType=1&shopId=cn.taobao.62301187&category_type=1&goods_id=13#{"from":"shihuo://www.shihuo.cn?route=goodsDetail","block":"Supplier","tp":"Supplier","sku_id":88366767,"extra":"2","dspm":"46e625b0904faa9c","pos_type":2,"goods_id":"13","supplier_id":"8234343","style_id":"6459093","size":"41","price":"1002","sort":"2","filter":"0000000","is_recommend":0,"goods_sku_id":12331971}链接拷贝到手机浏览器中自动跳转到淘宝,点击选项时加上了选择条件。
逐步删除条件,最终得到https://item.taobao.com/item.htm?id=643291979969&skuId=4798775291256&fromShType=1&goodsType=4&openType=1&shopId=cn.taobao.62301187&category_type=1&goods_id=13,一旦删除skuId将不能携带型号等属性自动选择。
真相
淘宝的skuId就是将信息同步到淘宝,淘宝将自动选中用户在识货选中的条件。

